One of the United States’ top carriers, Verizon, appears to be the victim of a data breach allegedly impacting millions of customers.
The SafetyDetectives cybersecurity team discovered a forum post on the clear web advertising a data dump allegedly containing the records of between 7.5 million and 9 million Verizon home internet and cellular customers.
According to the forum post’s claims, the information was “stolen by hackers” in January 2023.
While the information in the records does not appear to be particularly sensitive, according to our researcher, some of the data points could be merged with other leaks to impact customers significantly.
What is Verizon?
Verizon is one of the United States’ top carriers and one of the largest communication technology firms worldwide. Services on offer include cellular plans and broadband for consumers and the enterprise market.
The Fortune 500 organization reported $136.8 billion in revenue in 2022.
What and where is the forum?
The forum is available on the clear surface web. The platform operates message boards dedicated to database downloads, leaks, and cracks. There is also a dedicated marketplace for selling leaks, stolen account credentials, HackTheBox Flags – solutions for tackling Capture the Flag competitions – exams, and more.
Forum administrators claim that 14,919,292,019 records belonging to 887 datasets have been verified to date, although the claimed Verizon database is not on the list. Many other databases have been posted and available for download that are unverified.
Exposed information:
Our team’s investigation revealed the data dump contains datasets allegedly relating to approximately 1.5 million home internet customers from 2020, alongside roughly 7.5 million cellular plan subscribers from 2021 and 2022.

The forum post reads:
“Today I have uploaded the Verizon Database for you to download, thanks for reading and enjoy!
In January 2023, a database of 7.5 million customers belonging to Verizon was stolen by hackers.
Hashing: SHA256”
The forum post also mentions “Hashing: SHA256,” which indicates a level of encryption. However, according to our researcher only two columns in two separate data tables were hashed. The database, as a whole, was not protected by hash encryption.
Our researcher believes that the leaked database contains data stored by Verizon prior to January 2022. SafetyDetectives has reached this conclusion concerning the timeframe due to clues hidden in the filenames contained in the records. However, we cannot be conclusive with these indicators alone.
The size of the database is approximately 2.23GB. As shown below, there are two data tables of note.
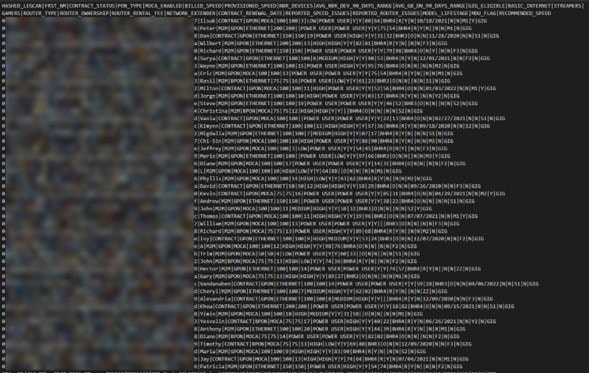
The first appears to relate to home internet subscribers, and contains information including first names, usage statistics, contract status, speed records, and router specifications.
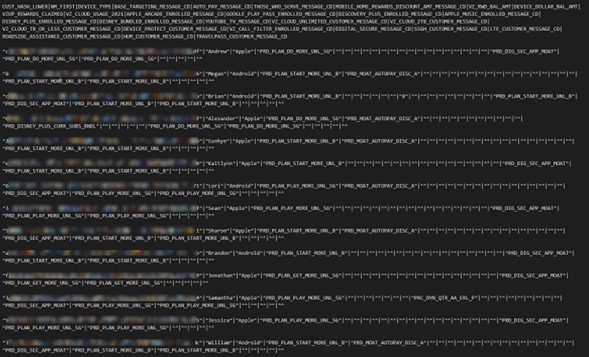
The second table allegedly contains data belonging to cellular network users. There appear to be records relating to customer hashes, device types, rewards and discounts, and whether or not subscribers are enrolled in services, including Apple Music, Disney+, YouTube TV, and Verizon cloud services.
The forum member – going under an offensive name – first joined in October 2022 and has since posted close to 500 times. Unlike many users who appear out of the blue on these types of forums, there may be more credibility attributable to this member due to their volume of posts and high reputation rating.
The alleged database was made available for download via an open link and with no paywall.
The impact of the data breach:
As the data dump was found on the clear, surface web, it is open, accessible, and available to download by forum members, but also to anonymous users, since the user posted the download link directly in the post body, which made it visible to anyone.
In the case of this specific post, the download link is public, free, and has not been otherwise locked or restricted.
Typically, these types of forums will throw up credit paywalls, in which users must purchase credits to obtain download links. Due to ethical reasons, our team will never pay for access to allegedly stolen databases. However, as the access was public, we downloaded the dataset for verification purposes, and only analysed a small sample.
While the information contained in the records does not appear to be highly sensitive or to contain Personal Identifiable Information (PII) – such as full names or physical addresses –
some of the data points could be merged with other leaks. For example, if combined with an existing PII leak, an attacker could have a higher chance of success in impersonating a customer.
It is not possible to verify whether the original database continues to be open and accessible today.
Vendor response:
Verizon was notified of the forum post on February 8. Unfortunately, at the time of writing, we have not received a response.
Timeline:
- January 2023: The month the alleged data breach took place
- January 27, 2023: The date the alleged data breach was posted on the forum
- February 7, 2023: The post was found by SafetyDetectives
- February 8, 2023: Verizon was notified of the forum post
A Verizon spokesperson reached out on March 7, 2023 with the following statement:
“First, this is old news. And it was not a breach of Verizon’s systems. Additionally, it was first reported in January. The bad actor continues to circulate it and pretending like it’s new. The fact is that it’s not.
As mentioned, this was not a Verizon breach, but an incident involving a third party vendor that formerly did business with Verizon. The company had very limited customer information, and they are no longer affiliated with our company. Verizon. Here’s was one story on it at the time.
Since then, there’s been an effort to recirculate this issue and material as if it’s new. The fact is that there’s nothing new here. The bad actor’s findings are being reposted, but it’s all recirculated material.
For awareness, the former vendor had no personal information such as customer addresses, social security numbers, banking information or credit cards. The data set only included the names and the type of Verizon plan that the customers were on. And much of the information was inaccurate, outdated and/or obsolete.”
Preventing data exposure:
When third parties hold your data, unfortunately, it is out of your hands when an organization exposes information. Here are some preventative tips followed by guidance on what to do after you are made aware of a data breach.
- Be cautious of what information you give out and to whom.
- Check that the website you’re on is secure by looking for HTTPS in the address bar, and/or a closed lock). This shows that communication has at least a basic level of encryption.
- Only reveal online what you feel confident cannot be used against you. Avoid sharing or posting sensitive PII, images, or personal preferences that could be troublesome if made public.
- Create secure passwords by combining letters, numbers, and symbols, and consider using a password locker to store complex combinations securely.
- Do not click links or respond to emails unless you know the sender is legitimate. Fraudulent links can send you to malicious websites or expose you to exploit kits, whereas phishing emails are designed to steal your information.
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust.
- Avoid using credit card information and typing out passwords over unsecured WiFi networks.
You can use tools including HaveIBeenPwned, as well as read our research and keep an eye on the news to find out if you are potentially involved in a data security incident.
If you suspect your data has been leaked, don’t panic. Nevertheless, it would be best if you tried contacting the organization responsible to discover exactly what happened. Furthermore, you should keep an eye on your credit report and your financial accounts for any signs of suspicious activity indicative of identity theft or fraud.
About us:
SafetyDetectives tests, compares, and reviews antivirus software, password managers, parental control apps, and virtual private networks (VPNs) using a robust testing methodology.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats. We aim to help the online community defend itself against modern-day cyberattackers while educating organizations on how to protect their users’ data.
Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware by following SafetyDetectives’ blog and our latest news.