
Intro
The SafetyDetectives cybersecurity team discovered a critical data leak affecting the prominent multinational security company, Securitas.
Securitas, based in Sweden, provides a full suite of security services and products for corporate clients across a range of industries.
One of the company’s Amazon S3 buckets was left open, exposing over 1 million files. The data we observed related to airport employees from different sites across Colombia and Peru, and there could be entities from other nations with exposed data on the bucket.
Moreover, we could not feasibly review every file on Securitas’ bucket due to the size of its logs and the sensitivity of its content. However, we believe other airports throughout Latin America may have been exposed in unseen files, and there’s a high probability that every Colombian airport which uses Securitas is ultimately affected.
Considering Securitas’ strong presence throughout Colombia and the rest of Latin America, companies in other industries could have been exposed. It’s also probable that various other places that use Securitas’ security services are affected.
The nature of the exposed data may pose a serious threat to airports, airlines, passengers, and staff should a malicious actor have accessed the bucket’s content while it was still unprotected.
Who Is Securitas?
Founded in 1934, Securitas is a huge multinational corporation and a superpower within the security services industry. The company is headquartered in Stockholm, Sweden, and has branches located around the world. These include a European segment, a North American segment, and an AMEA division (Africa, the Middle East, Asia, and Australia). Securitas’ data exposure is thought to impact clients in its Ibero-America segment—the portion of Securitas’ business that works within Latin America.
Securitas has a strong presence in Colombia with offices in several locations. The company provides services to a range of industries in Colombia and throughout South America, though, affected businesses seemed to work within the aviation industry only.
Securitas currently employs over 350,000 people in 48 markets, and this enormous workforce helps the company serve around 150,000 clients worldwide. In 2020, Securitas generated sales of MSEK 107,954 (over US$11.9 billion) with an income before tax of MSEK 3,329 (over US$369 million).
Securitas’ services cover four key areas: On-site guarding, electronic guarding, fire and safety, and corporate risk management. The company provides a range of specific products to meet these needs, including trained security staff, video surveillance, alarm patrolling, electronic access control, fire and safety risk management, and supply-chain risk management.
Securitas works with clients across practically every industry, from construction to retail, maritime, and even residential. In the aviation industry, Securitas provides specialized solutions, such as baggage screening.
We know the bucket belongs to Securitas because of application IDs within mobile apps located in the bucket.
What Was Leaked?
Securitas left its Amazon S3 bucket open and accessible, without any authentication procedures in place. The misconfigured bucket has therefore exposed almost 1.5 million files, equating to about 3TB of data.
The bucket’s exposed information included employee PII and sensitive company data of at least four airports in Colombia and Peru: El Dorado International Airport (Bogota D.C, COL), Alfonso Bonilla Aragón International Airport (Valle del Cauca, COL), José María Córdova International Airport (Antioquia, COL), and Aeropuerto Internacional Jorge Chávez (Lima, PE). As mentioned, unobserved files may have exposed other airports and places throughout Colombia, the rest of Latin America, or even the rest of the world.
We observed two main datasets containing the information of Securitas employees and airport employees: photos of ID cards and other unmarked photos.
Photos of ID cards featured on the bucket. There were an estimated 1 million files of this type on Securitas’ misconfigured bucket. These files revealed the personal information of employees at the four aforementioned airports that are using Securitas’ services.
Photos of ID cards reveal several forms of employee PII, including:
- Full names, incl. first names and surnames
- Photos of employees
- Occupations
- National ID Number
Other unmarked photos featured among the bucket’s content too. There were about 300,000 files of this type. These photos leaked the data of airports, airport employees, and associated companies.
Specifically, these files exposed employees’ personal data, sensitive client data (airports), and the sensitive data of associated companies, such as airlines. Exposed data includes:
- Photos of employees
- Photos of planes
- Photos of fueling lines
- Photos of luggage being loaded/unloaded
In addition to the information mentioned above, the two primary datasets analyzed on the bucket (photos of ID cards and other unmarked photos) contained Exchangeable Image File Format (EXIF) data that exposed specific information related to each photo.
Exposed EXIF data includes:
- Device models (of the cameras used)
- GPS locations of photos, incl. coordinates and GPS maps
- Time & date of photos
Note: Securitas’ bucket contained another form of data: Android mobile apps that are used by security personnel to help with various tasks, such as incident reporting. While the presence of these apps doesn’t expose any specific forms of sensitive data, they could be used to aid in criminal activities.
The bucket was live and being updated at the time of discovery. The misconfiguration of Securitas’ Amazon S3 bucket is not the responsibility of Amazon and this breach is not Amazon’s fault.
We mentioned that the bucket’s content included data from at least four airports that are Securitas clients. A significant portion of the data we examined relates to El Dorado International Airport, located in Bogota D.C, Colombia. Note: there was data from other airports and airport personnel exposed, too.
Photos of ID cards were the largest dataset we observed on Securitas’ bucket. The IDs we saw belonged to El Dorado airport staff along with personnel from various airports and private companies. You can see evidence of photos of ID cards below.

An ID for an El Dorado employee (Securitas)

An ID belonging to a Civil Aviation Authority of Colombia employee
Other unmarked photos exposed data for Securitas clients, airport employees, and associated businesses. There was no indication in file names regarding the purpose of these photos, although, one could assume they were collected for a security assessment.
Exposed employees are not just official airport staff but include staff from several different private companies, one of which was Securitas. There were photos of people, places, planes, and various other airport functions on the bucket.

A different type of ID card found among the files

An airport employee from a private company is pictured

A plane’s landing carriage and fuel line

A shot of an employee loading luggage
EXIF data detailed a variety of information specific to each image. EXIF data wasn’t stripped from photos and, therefore, was exposed along with images on the open bucket. You can see examples of EXIF data in the following screenshots.
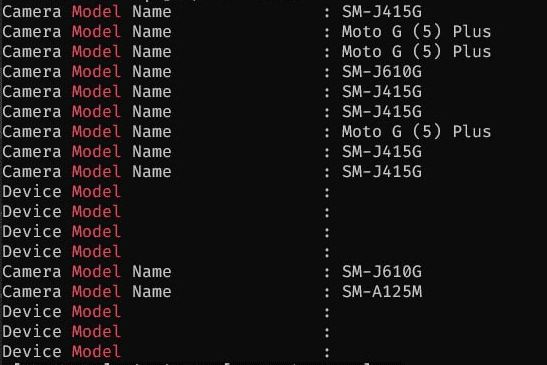
Camera models were identifiable in EXIF data
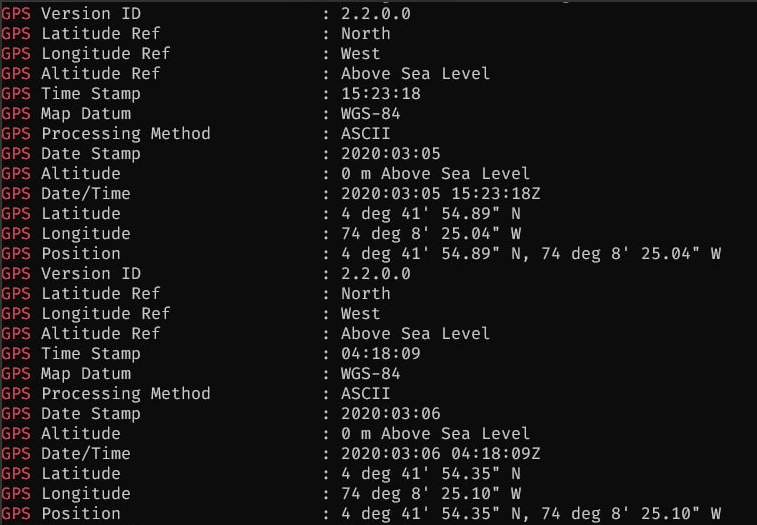
GPS information and time stamps were also found in EXIF data

A GPS map of one photo’s location
Though an exact estimate of the number of people affected is difficult to attain, we believe a huge number of companies and employees across potentially numerous industries may be exposed. We have analyzed data relating to four airports that are impacted, though, we think there could be many more affected parties.
Furthermore, airports, companies, and employees from several Latin American countries, as well as other parts of the world, could potentially be exposed. We have observed data belonging to entities from Colombia and Peru.
You can see a breakdown of Securitas’ data breach in the following table.
The SafetyDetectives cyber-security team found Securitas’ Amazon S3 bucket on October 28th, 2021. Content on the bucket dated back to November 2018. However, we do not know how long the bucket had been left open.
We sent a responsible disclosure of the data exposure to Securitas on October 28th, 2021. Securitas replied a day later, telling us to disclose the breach to a different company email address (which we did on the same day). On November 1st, 2021, we sent a follow-up message to Securitas as the bucket was still unsecured, and we also disclosed the breach to the Swedish CERT.
Securitas replied on November 2nd, 2021, and the open AWS S3 bucket was secured. The Swedish CERT also replied on this day, though, their message came after Securitas had closed the bucket.
Securitas and its clients could face several impacts due to this data breach.
Data Breach Impact
We do not and cannot know whether bad actors have accessed the bucket’s content.
In the case that malicious parties have accessed Securitas’ bucket, the content thereof could pose a security threat to the four (or more) leaked airports, along with airport employees and companies. Securitas may face legal sanctions and various impacts because of its breach too.
Impact on Clients and Companies
Securitas’ data breach poses a risk to the four leaked clients: El Dorado International Airport (COL), Alfonso Bonilla Aragón International Airport (COL), José María Córdova International Airport (COL), and Aeropuerto Internacional Jorge Chávez (PE).
The impact of this breach spreads further than these organizations alone, affecting a range of other private companies.
Airport security protects the lives of travelers and airport staff. As such, this breach is extremely dangerous with potentially devastating consequences should the bucket’s content end up in the wrong hands. Both within Colombia and around the world, there are guerrillas and terrorist organizations that could cause a huge amount of damage if they accessed Securitas’ bucket.
For this reason, security infiltration is the number one risk associated with Securitas’ clients and associated companies. Photos of IDs and employees could allow criminals to impersonate various members of staff—employees that can gain access to restricted areas of the airport, such as luggage-loading areas and even planes. Criminals could even use leaked data to create counterfeit ID cards and badges. A criminal could further strengthen their appearance as a legitimate employee by downloading leaked mobile apps.
In the worst-case scenario, airport employees could come face-to-face with violent criminals. This means airport employees are potentially at risk of physical and psychological harm. Criminals could abuse airport staff to find out information, such as mobile app credentials or access codes for locked doors. Criminals could also take employees hostage (or even kill employees) to prevent them from fighting back.
Criminals could use other unmarked photos on the bucket to gather intel about the airport for a planned infiltration. Bad actors could use this access to steal large quantities of possessions or goods. Though, the security implications for airports and airlines here are potentially far more serious.
On a side note, bad actors with financial motives could target companies with fraud and scams. Bad actors could use leaked PII to pose as a colleague or customer. Once bad actors gain the trust of airport staff, they can attempt to trick victims with popular scams. For example, bad actors could convince companies to pay fake invoices for services.
Impact on Securitas
Securitas had employee data and sensitive information exposed on the bucket and, therefore, could also come under threat of the above-mentioned criminal activities.
Elsewhere, Securitas could face sanctions for data protection violations should regulators decide the company has broken the law.
Securitas’ data breach has exposed the information of Peruvian and Colombian citizens (if not more) and organizations within national borders. This means Securitas could be subject to punishments from the Autoridad Nacional de Protección de Datos Personales (ANPDP) of Peru and the Superintendent of Industry and Commerce (SIC) of Colombia.
The ANPDP could impose sanctions of up to S/ 220,000 to S/ 440,000 (approx. US$61,000 to US$122,000) should they find Securitas’ breach is a “very serious” violation of data protection laws. Peruvian authorities could impose additional fines of S/ 44,000 (approx. US$12,200) for any continued breach of data protection regulations.
The SIC of Colombia can impose a maximum fine of 2,000 minimum legal monthly salaries (equivalent to approx. US$400,000) for a breach of data protection regulations, with successive fines for any continued violations.
Preventing Data Exposure
What steps can we take to make sure our personal data is protected? And what can we do to minimize the impact of cybercrime?
Here are a few tips to prevent data exposure:
- Only provide your sensitive and personal data to companies/individuals you can completely trust.
- Make sure the website you’re using is secure. Secure websites have a “https” and/or a closed lock symbol before their domain name.
- Do not provide entities with your most sensitive information—data that could easily be used against you to a damaging effect (i.e. government ID numbers, social security numbers, and preference).
- Use letters, numbers, and symbols to create secure passwords.
- Don’t click links in emails, messages, or on websites when you can’t completely trust the source.
- Make sure your privacy settings on social media sites only show your information to trusted users.
- Avoid using credit cards or typing out passwords when connected to unsecured or public Wi-Fi networks.
- Educate yourself on data protection, cyberthreats, and everything you can do to avoid data exposure and cybercrime victimization.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.