A publicly-listed multinational retailer with millions of dollars in annual revenues was discovered to be operating a completely unsecured server, thereby publicly exposing private data belonging to around 700,000 of its customers.
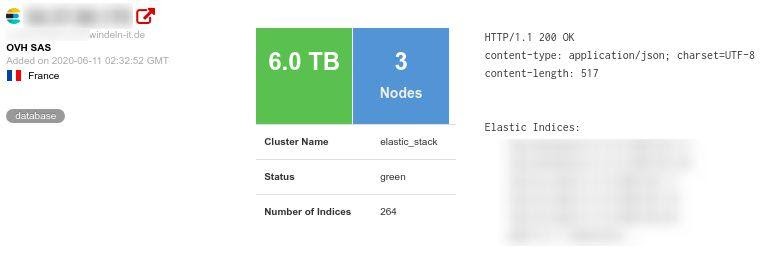
Our Security team, led by Anurag Sen, discovered a vulnerable and unsecured server containing more than 6 terabytes of data operated by German company windeln.de.
Our team detected the breach on 13 June 2020 and estimates that the server vulnerability was exposed on the Internet on 11 June 2020.
The ElasticSearch server and its vulnerability were discovered during a routine check of IP addresses on particular ports. Our team found that the server was completely unsecured and publicly exposed without a password – meaning that anyone in possession of the server’s IP address could access the entire database.
We tried to reach out to Windeln.de, but nobody ever got back to us. We then contacted the German CERT, so they could inform the company about the data leak. A few days later, the server got secured.
Who is windeln.de?
First established in 2010, ‘windeln.de’ is a German-based retail company with an online shopping portal catering for baby and toddler products in Europe. The company also operates a large cross-border e-commerce business between Europe and China.
The company operates several online mail-order hubs, namely: windeln.de, windeln.ch and Bebitus with China standing as the largest sales market for windeln.de.
Popular products sold via windeln.de include diapers, baby food, children’s furniture, toys, clothing, baby monitors, children car seats as well as cosmetic and partnership products for parents.
The parent company claims to serve around 700,000 customers with 40 distinct brands in 7 countries. In 2019, windeln.de generated revenues of €82 million and is currently publicly listed on the Frankfurt stock exchange.
What was leaked?
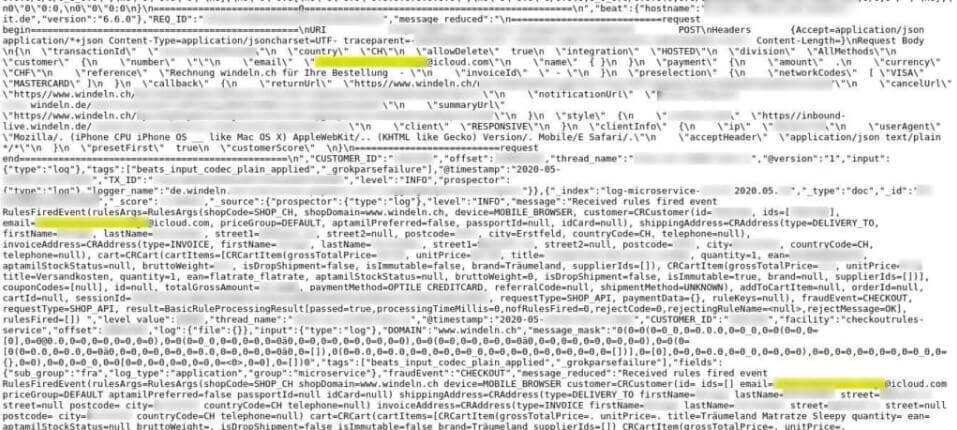
The server contained relevant API logs from the company’s web and mobile sites, thereby exposing all production server information.
Our team discovered a database with more than 6.4 terabytes of data and found that different ports allowed access to different tranches of data.
In total, the database contained a total record count running in excess of 6 billion. The database is a production server which stored data from 24 May 2020 until the present day, and contained “backlog” information including API and internal logs with user/customer details.
User detail with hashed password
A detailed list of the type of information found on windeln.de’s server is presented here:
- Full names
- Email addresses
- Full postal addresses
- Telephone numbers
- IP addresses
- Windeln.de newsletter subscription mailing list
- Order and purchase details
- Payment methods (without payment information)
- Order invoices
- Information about users’ children including their names, dates of birth and gender information
- Amazon OAuth API login tokens
- Authentication tokens
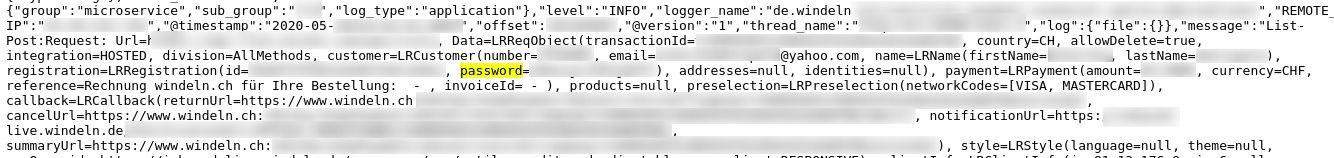
- Partial listings of hashed passwords
- Internal logs including various employee details
- Logs referring to sister site and brand Bebitus.com including website user account tokens
is a Spanish version of the sister site and brand being marketed by windeln.de.

Record of Bebitus account tokens
Other site brands were often referred to in the logs, such as windeln.com.cn and windeln.ch.
Our security team found around 98,000 entries including emails, full names and user IP addresses although some records were missing, duplicated or invalid.
Crucially – and raising the level of risk created by the leak – several information records referred to children whose parents were using the site. Records showed full names, dates of birth and gender information.
Information relating to children is particularly sensitive because malicious hackers can exploit the strong bond between parent and child, by, for example, using the child’s birthday as an opportunity to deploy scams upon the parents. For example, a nefarious individual could use the birthdate to dupe the target into believing they are genuine and exploit that sense of loyalty to deploy various scams via email/telephone or in person.
Around 1,500 entries included emails, full names, phone numbers, addresses, payment methods, order date, product info, customer ID and language preference. However, our security team confirmed that in general, the breach revealed partial records only, so not all pieces of information were available for all users.
Also, our team reported that around 128,000 instances of personal information were exposed specifying subscription status, email addresses, full names, IP addresses and order history across windeln.de’s site network.
Overall, it is difficult to clarify exactly how many users were affected by the vulnerability although windeln.de states it has served 700,000 customers to date.
Some users had every piece of data exposed (as listed above), whereas others, only had some exposure (presumably because they did not specify all their personal information when signing up and shopping via windeln.de).
Data Breach Impact
The impact of this data breach on users could have been severely problematic for windeln.de and its customers. However, at this stage, it is unknown whether the data made available in the leak was obtained by any third parties or malicious users.
One of the biggest dangers, in this particular case, is the personal impact on users.
Thankfully, financial records such as payment details or credit card numbers were not leaked – however, a vast amount of personal information means hackers can target a particular individual with phishing, phone and malware scams.
An affected user could be contacted by a hacker pretending to be from windeln.de and with the use of seemingly innocuous data such as purchase history, could convince the user into divulging much more critical data such as financial information or copies of government-IDs. Another more sophisticated scam is to send an email showing windeln.de branding and their personal information to incite a click-through. Upon visiting an unsecured website, hackers could potentially install malicious software on the visitor’s computer and thereby gain deeper access to someone’s life.
The threat of identity theft and fraud is persistent when private data is unsecured and unencrypted. Having access to user’s personally identifiable information including contact details and purchase history could be used to assist in fraud and different kinds of identity theft across other sites and establishments.
Another critical risk created as a result of the server being left unsecured is further attacks on windeln.de and its network of sites. Several back-end technical logs expose not only personal information, but also, information that could potentially be harnessed (and weaponised) to obtain deeper control of the server. In these cases, ransomware attacks could be carried out which often leads to severe and irreparable damage to brands and company operations.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you are not a victim of attacks – cyber or real-world – if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you are on is secure (look for https and/or a closed lock)
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.)
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecured Wi-Fi networks
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware
About Us
is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data.
Published on: Sep 15, 2020