
SafetyDetectives spoke with Bulent Kocaman, PD Hosting director and IT veteran with over twenty years of experience. He explained in detail the security measures applied by a web hosting provider with a decade of experience, and added a full security guide for PHP application developers.
What hosting services are you currently offering?
At PD Hosting, we pride ourselves on offering an extensive array of hosting solutions tailored to serve a wide range of client requirements. Here’s a deeper dive into our main service categories:
Web Hosting
Our standard web hosting packages are engineered for versatility and ease of use. They are perfect for small to medium businesses and individual portfolios. With features like LiteSpeed Web Server for enhanced speed, free SSL certificates for security, and cPanel for easy management, we aim to provide an all-in-one package that combines performance with simplicity.
WordPress Hosting
Our specialized WordPress hosting is built to provide an optimized environment specifically for WordPress websites. From one-click installations to automated backups and updates, we take care of the technicalities so that you can focus on content creation. The service is fortified with additional layers of security to protect against WordPress-specific vulnerabilities.
Application Hosting
Our Application Hosting service is tailored for clients running specialized web applications built on platforms such as WooCommerce, Magento, Drupal, PrestaShop, OpenCart, and Joomla. These aren’t just generic hosting plans; they are optimized environments designed to make these specific applications run at peak performance. With features aimed at both speed and security, our Application Hosting solutions offer a robust and reliable home for your specialized web projects.
Linux VPS
Geared towards tech-savvy users and enterprises, our Linux VPS service offers a customizable environment with root access, allowing for complete control over the operating system and installed software. Real-time monitoring and usage graphs are available through our PD Hosting dashboard, providing insights into your server’s performance.
WordPress VPS
For those who require a dedicated, high-performance hosting solution for their WordPress sites, our WordPress VPS is the answer. This service combines the customization options of a VPS with optimizations specifically geared for WordPress, ensuring maximum performance and security.
Additional Services
Beyond these core hosting solutions, we offer a multitude of other services designed to provide a complete, end-to-end experience for our clients:
- Domain Name Registration: As an accredited member of Nominet, we’re a trusted UK Domain Registrar, offering a wide array of domain extensions including UK-specific ones. In total, you have the choice of over 200 TLDs, ensuring you can find the perfect domain name to represent your brand or idea, whether it’s a UK-specific domain or a more general TLD.
- Professional Email via OX App Suite: Currently, our flagship professional email service is powered by OX App Suite, offering a feature-rich experience that includes shared calendars, tasks, and more to elevate your business communication. We’re also excited to mention that we are in the process of broadening our email solution offerings to provide even more options tailored to diverse business needs.
- DNS Manager: Our DNS Manager tool is not just about basic DNS settings; it’s a comprehensive solution that provides you with extensive control over your domain’s routing. Alongside standard configurations, it offers Domain and Email Forwarding options for added flexibility. For peace of mind, we also provide automatic and manual DNS backup and restore capabilities, ensuring that you can easily recover from any mishaps or changes.
- Website Maintenance Packages: For those who prefer a hands-off approach, our website maintenance packages offer regular updates, backups, and other essential upkeep services.
- Make Me A Website: A complete design, development, and support service that delivers a fully functional website tailored to your specific needs.
- Website Builder: For those looking to take a more DIY approach, our intuitive Website Builder tool makes it easy to create a professional-looking website without the need for coding skills.
- WordPress Manager: Our WordPress Manager is more than just a convenience—it’s a full-fledged tool designed to give you comprehensive control over your WordPress site. You’ll find standard offerings like one-click installations and updates, as well as a curated selection of pre-installed plugins and themes to get you started. But where our WordPress Manager truly shines is in its advanced features. You can easily test changes with our Staging & Cloning options, streamline your website’s launch with Easy Go Live, and even import your existing WordPress site from external sources. Security is also a focal point, with features like Single Sign-On (SSO) and Website Speed Monitoring. Troubleshooting is simplified with Debug and Maintenance Modes, and you can capture images of your site for record-keeping or for troubleshooting future issues. With additional utilities for Backup & Restore and Plugin & Theme Management, our WordPress Manager aims to offer a truly holistic experience, saving our clients both time and effort.
- Easy Browser-Based SSH Connections to VPS: For advanced users, we offer the convenience of initiating SSH connections to your VPS directly through the browser, streamlining the management process.
- Security and Backup Services: Security is never an afterthought at PD Hosting; it’s an integral part of our service offerings. We provide a robust suite of security measures that includes SiteLock for real-time malware scanning and CodeGuard for automated backups, both designed to give you peace of mind about the safety of your digital assets. For our Web, Application, and WordPress hosting solutions, we take it a step further by incorporating JetBackup for additional backup options. The hosting environments are also fortified with CloudLinux and Imunify360, offering layered security measures that protect against various vulnerabilities and attacks.
By offering these additional services, PD Hosting aims to be a one-stop-shop for all your online needs, making it easier for you to manage and grow your digital presence.
Each of our hosting solutions is designed with scalability in mind, allowing you to effortlessly upgrade as your business grows, all while maintaining the highest levels of security and performance.
What security measures have you implemented to protect your customers’ data?
At PD Hosting, data security is one of our highest priorities. We employ a multi-layered approach to protect customer data, leveraging both technical and procedural safeguards.
Infrastructure: Our foundational infrastructure is built on AWS, which is globally recognized for its high levels of security and reliability. This strong base is complemented by additional trusted technologies such as CloudLinux, cPanel, and Imunify360.
KernelCare: We use KernelCare to apply crucial kernel updates without requiring system reboots, ensuring both uninterrupted service and a secure environment.
Encryption: All data transfers between our servers and clients are safeguarded through high-grade SSL/TLS encryption protocols.
Firewalls & Intrusion Detection: Advanced firewalls and intrusion detection systems are in place to monitor and control incoming and outgoing network traffic based on an array of security rules.
Anti-Malware Scanning: In partnership with SiteLock, we perform real-time malware scanning to identify and promptly mitigate any threats.
Automated Backups: Our default backup system includes JetBackup and our own proprietary backup solutions, which cover websites, DNS, and databases.
Server Environment: With CloudLinux and Imunify360, we offer advanced security features like real-time malware scanning and threat detection.
From a procedural standpoint, we’ve implemented rigorous internal policies that govern data access and management. We limit the number of employees who have access to confidential data and regularly update our staff on best security practices.
Additionally, our registration with the Information Commissioner’s Office (ICO) in the UK serves as a testament to our commitment to comply with strict data protection laws and regulations.
Through the integration of these technical and procedural measures, we strive to provide an environment that our clients can unequivocally trust.
What does your disaster recovery plan look like, and what do you suggest your users do to be ready?
Our disaster recovery strategy at PD Hosting is both robust and flexible, capable of handling a variety of scenarios—from simple data corruption to more complex, widespread issues. We leverage AWS’s inherently secure and resilient infrastructure, which includes data redundancy and failover capabilities across multiple geographical regions. This ensures data integrity and availability at all times. We also conduct regular drills to test our disaster recovery protocols, ensuring they remain current and effective.
For our users, the first step in being prepared is to utilise the automated backup solutions we offer. Multiple backup copies make it easier to restore your system to a functional state should the need arise. We also recommend familiarising yourself with our recovery processes; we offer extensive documentation and customer support to walk you through any steps you may need to take in a crisis. And it’s essential to keep your contact details up-to-date in your Pdhosting.co.uk client portal so we can communicate effectively in any emergency situation.
So, being prepared isn’t just about having a plan in place; it’s about making disaster recovery part of your operational mindset. This way, we’re all better equipped to handle unforeseen challenges.
How do you stay updated with the latest security threats and vulnerabilities in the web hosting industry?
Keeping abreast of the latest security threats and vulnerabilities is an ongoing commitment. We rely on a variety of trusted sources for timely and accurate information. This includes subscribing to security bulletins, reading whitepapers, and participating in specialised forums and advisory groups online.
Vendor relationships are another key aspect. Since we work closely with the leading technology partners, we get timely updates on security patches and best practices, which allows us to act swiftly when new threats emerge. Whenever new patches or security measures are released, we are among the first to know and can take immediate action.
Internally, we prioritise regular training to keep our team updated on the latest in security protocols and measures. This ensures that everyone, from customer service representatives to the technical staff managing our infrastructure, is aligned in maintaining the highest standards of security.
It’s a dynamic, ever-changing landscape, but our proactive approach helps us stay ahead of the curve, ensuring that we provide a secure and reliable hosting environment for our clients.
Could you give us an overview of the technology stack that PD Hosting employs for optimal performance and security?
Our infrastructure is designed for both high performance and robust security, with AWS serving as the backbone for our services. While we do utilise cPanel, one of our standout features is our custom control panel. This offers our clients an intuitive interface that negates the need to interact directly with cPanel, streamlining the hosting management process.
For the server environment, we rely on a combination of CloudLinux, LiteSpeed, and KernelCare. CloudLinux isolates each hosting account for heightened security and resource allocation. LiteSpeed serves as our web server, and we enhance its capabilities with LiteSpeed Cache (LSCache) for optimised website speed. KernelCare allows us to update the server kernel without requiring reboots, which means better security and uptime.
Our email service is powered by MailChannels, ensuring reliable email delivery. On the security front, Imunify360 is our go-to for real-time firewall protection, intrusion detection, and malware scanning. We back up data using both JetBackup and our own proprietary backup systems.
On the development side, we’ve built various APIs and microservices, primarily using Symfony and Laravel frameworks. We also make use of modern technologies like Swagger for API documentation, API Platform for streamlined API development, and frontend technologies like NodeJS and Vue.js.
So, our technology stack isn’t just about individual components; it’s about how they all integrate to create a secure, reliable, and high-performing environment for our clients.
What security challenges and exciting developments do you see in the future of web hosting, and how do you plan to cope?
The web hosting industry is in a constant state of evolution, especially when it comes to security challenges. One growing concern is the increasing sophistication of cyber-attacks, including ransomware and DDoS attacks. Additionally, as more businesses move to the cloud, ensuring the security of cloud-based services becomes even more critical.
On the exciting side, developments like AI and machine learning are offering new ways to detect and prevent security incidents. Automated threat detection and real-time analytics are becoming more accurate and faster, thanks to these technologies.
At PD Hosting, we’re actively investing in R&D and keeping a close eye on emerging technologies. We’re exploring ways to integrate machine learning algorithms for improved security monitoring and incident detection. We’re also looking into enhancing our services with more advanced encryption methods to protect data integrity.
Moreover, we plan to continue our strategy of proactive education, both internally among our team and externally for our clients. This involves keeping everyone up-to-date on the latest security practices and encouraging a culture of security awareness.
Our aim is not just to adapt to the evolving landscape but to be a step ahead, ensuring that we offer our clients a hosting environment that is both secure and equipped with the latest technological advancements.
Are there any new services or features that PD Hosting is planning to roll out in the near future?
Absolutely, the future at PD Hosting is brimming with innovation and expansion. One of our most notable upcoming features is a cryptocurrency payment gateway, which we are actively developing in-house. This not only adds another dimension to our payment options but also showcases our capabilities in software development and our commitment to embracing new technologies.
Artificial Intelligence is another frontier we’re exploring extensively. We have already partly implemented AI into our operational workflow and have plans to extend this across various other functionalities, including advanced security monitoring and automated customer service solutions.
In terms of email services, we’re in the process of rolling out an alternative professional email solution. This new service will sit alongside our existing offerings, providing a more diversified portfolio for our clients to choose from.
We’re also introducing DirectAdmin as an alternative control panel, complementing our existing cPanel offerings. This will cater to clients who may prefer a different server management interface and add another layer of customization to our services.
On the subject of customization, we’ve already been offering specialised hosting solutions for various applications, including e-commerce, and we’re continuously working to enhance these services even further.
We pride ourselves on being a one-stop solution provider, capable of developing and supporting a wide range of client needs in-house. This includes everything from custom hosting solutions to specialised application development.
Another exciting development on our roadmap is the expansion of our VPS offerings. We’re in the process of deploying a variety of pre-defined VPS solutions that cater to specific applications, workloads, and business needs. Whether you’re running a high-traffic e-commerce site, a data-intensive application, or simply need a tailored solution for your unique business requirements, our expanded VPS offerings will provide the flexibility and performance you need.
Additionally, we’re looking into expanding our geographic reach by offering hosting solutions that are optimised for different regions, ensuring lower latency and better local compliance.
We’re also committed to enhancing our customer service experience. Future plans include the introduction of a more comprehensive knowledge base and possibly a community forum where users can share tips, tricks, and solutions.
So, as you can see, our roadmap is filled with initiatives aimed at making our services more robust, versatile, and user-friendly. We’re not just adapting to the industry’s evolving landscape; we’re aiming to be pioneers, leading the way in offering cutting-edge, secure, and reliable hosting solutions.
Given your extensive experience, what advice would you offer to aspiring PHP developers in the context of cybersecurity?
When it comes to PHP development in the context of cybersecurity, my first piece of advice is to never underestimate the importance of writing secure code. In today’s world, security isn’t an afterthought; it should be integrated into the development process from the start.
For aspiring PHP developers, I would highly recommend becoming familiar with the OWASP Top 10 list of web application security risks. Understanding these common vulnerabilities, such as SQL injection and cross-site scripting, can help you recognize and prevent security flaws in your code.
Another critical practice is input validation. Never trust user input; always validate and sanitise it. This applies to anything from form submissions to URL parameters. Using built-in PHP functions like `filter_var()` or utilising frameworks that have secure input handling can go a long way.
Also, focus on secure session management. Session hijacking is a common attack vector, so use secure, random session IDs, employ session timeout policies, and ensure secure cookie flags are set.
Lastly, stay updated. Cybersecurity is a constantly evolving field, and what was considered secure yesterday may not be tomorrow. Keep abreast of the latest security updates, follow well-known PHP security blogs, and, if possible, participate in PHP and cybersecurity communities online to learn from experts and peers.
By adhering to these practices and staying vigilant, you’re not just writing code; you’re contributing to the overall security posture of the applications you’re developing.
What coding standards or frameworks do you recommend for developing secure PHP applications?
For secure PHP development, I highly recommend following specific coding standards, especially those like PSR-1 for basic coding standards, PSR-2 for coding style, and the updated PSR-12, which extends and supersedes PSR-1 and PSR-2. These standards are put forth by the PHP Framework Interoperability Group (PHP-FIG) and are instrumental in improving code quality, readability, and security.
One of the advantages of using frameworks like Symfony and Laravel, which we frequently use at PD Hosting, is that they’re designed to comply with these and other PSR standards. This sets up a strong foundation for developers, allowing them to focus on writing secure and maintainable code that aligns with best practices in the industry.
While we’re on the subject of frameworks, it’s worth noting that Symfony and Laravel have specific features that enhance security. Symfony has a Voter system that allows for complex access control rules, while Laravel’s Eloquent ORM uses prepared statements which help in preventing SQL injection attacks.
Earlier, I touched on the importance of input validation. In addition to PHP’s native filter_var function, both Symfony and Laravel offer their own validation logic, which is more robust and often easier to implement, thereby enhancing security.
Another vital element in secure PHP development is dependency management. Tools like Composer are invaluable for this, helping you to manage your project’s libraries and dependencies while also enabling you to keep them updated and secure.
Automated testing and static analysis tools are also critical for maintaining a secure codebase. Tools like PHPUnit for unit testing and PhpStan for static code analysis can be integrated into your development workflow to automatically identify potential security risks.
So, in wrapping up, focusing on the right frameworks, adhering to industry-standard coding practices, and employing secure and updated libraries are crucial steps in developing secure PHP applications.
Could you walk us through a practical example that outlines best practices for securing a PHP application against common vulnerabilities?
Securing a PHP application requires a layered approach that addresses multiple aspects of security. From sanitising user input to implementing strong authentication mechanisms, each layer adds an additional hurdle for would-be attackers. While the examples provided here are meant to introduce you to some best practices, it’s worth noting that using a well-established framework often comes with built-in security features that can save both time and effort. Now, let’s delve into some of these crucial security aspects to provide you with a comprehensive understanding of how to better secure your PHP applications.
The Importance of Security in PHP Applications
Security is not an afterthought; it’s a fundamental aspect of any robust application. In the PHP ecosystem, where the language itself has evolved significantly in terms of security features, it’s crucial to stay updated and vigilant. PHP, being a server-side scripting language, is often exposed to various types of vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF), among others. These vulnerabilities can compromise not just the application but also the data it holds, affecting both your business and your users.
Take, for example, an e-commerce site that handles sensitive customer data and financial transactions. A single vulnerability can not only result in financial loss but also severely damage the brand’s reputation. Here at PD Hosting, we take a proactive approach to security, implementing layered security measures to mitigate such risks.
Understanding the importance of security in PHP applications sets the stage for adopting the right strategies and tools to build a secure application. This underscores the need for every PHP developer to be well-versed in security best practices from the get-go.
Sanitising User Input: The First Line of Defense
User input is one of the most common vectors for security vulnerabilities, often serving as an entry point for attacks like SQL injection and Cross-Site Scripting (XSS). The first step in securing your PHP application is to treat all user input as untrusted data.
Code Example: Using `filter_var()`
Consider the following example where we use PHP’s built-in `filter_var()` function to sanitise email input:
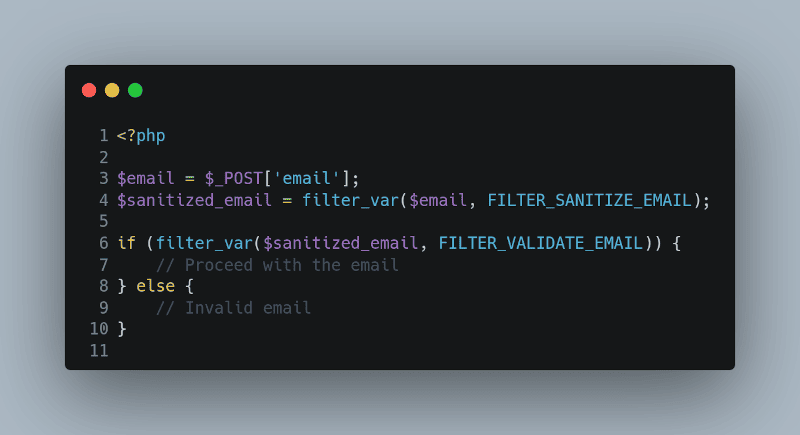
$email = $_POST[’email’];
$sanitized_email = filter_var($email, FILTER_SANITIZE_EMAIL);
if (filter_var($sanitized_email, FILTER_VALIDATE_EMAIL)) {
// Proceed with the email
} else {
// Invalid email
}
In this example, the `FILTER_SANITIZE_EMAIL` filter removes all illegal email characters from a string. Following that, `FILTER_VALIDATE_EMAIL` is used to validate the sanitized email.
Framework-Level Validation
If you’re using a framework like Laravel, you can take advantage of its built-in validation methods:
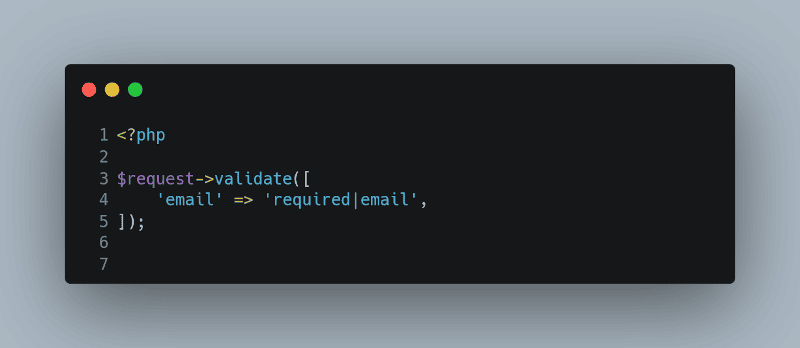
$request->validate([
’email’ => ‘required|email’,
]);
Laravel’s validation methods are compliant with best practices, making it easier to implement complex validation logic securely.
Always Validate on the Server Side
While client-side validation can improve user experience by providing immediate feedback, it should never replace server-side validation. An attacker can easily bypass client-side validation by directly interacting with your server.
By rigorously sanitising and validating user input, you form the first, critical line of defence against potential attacks, thereby enhancing the overall security of your PHP application.
Preventing SQL Injection: Parameterized Queries and Prepared Statements
SQL injection is a prevalent security vulnerability that occurs when an attacker is able to manipulate a SQL query by injecting malicious SQL code. This can lead to unauthorised access to your database, data leaks, and even data loss. To mitigate this risk, it’s crucial to use parameterized queries or prepared statements.
Here’s a simple example in PHP using PDO (PHP Data Objects):
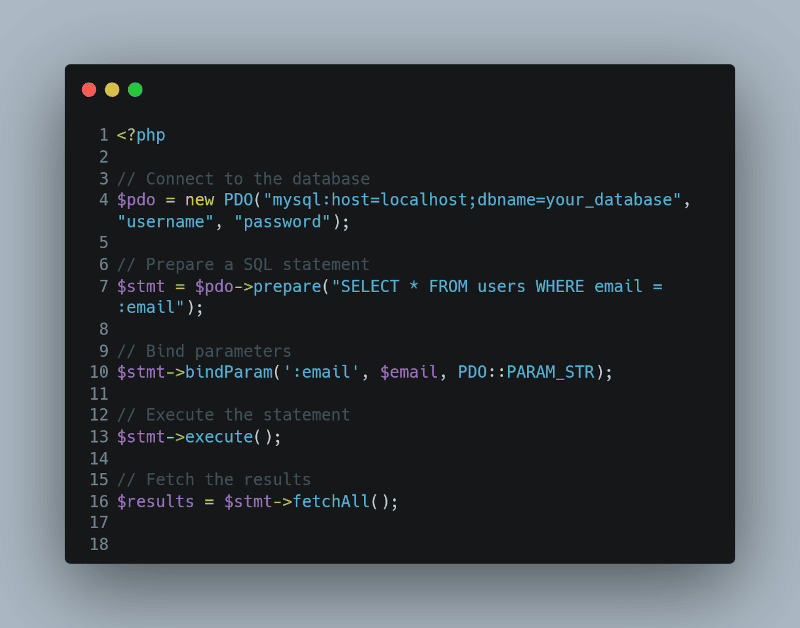
<?php
// Connect to the database
$pdo = new PDO(“mysql:host=localhost;dbname=your_database”, “username”, “password”);
// Prepare a SQL statement
$stmt = $pdo->prepare(“SELECT * FROM users WHERE email = :email”);
// Bind parameters
$stmt->bindParam(‘:email’, $email, PDO::PARAM_STR);
// Execute the statement
$stmt->execute();
// Fetch the results
$results = $stmt->fetchAll();
In this example, the :email is a placeholder for the actual email value, which is bound to the SQL statement using the `bindParam()` method. This ensures that the SQL query is not directly exposed to user input, making it far more difficult for an attacker to inject malicious SQL code.
By consistently using parameterized queries and prepared statements, you not only make your PHP application more secure but also make your code more reusable and easier to maintain.
Securing Session Data: Best Practices for Session Management
Session management is vital for maintaining state between multiple requests from the same user. While PHP’s built-in session handling provides a good starting point, there are several best practices to follow to ensure that session data remains secure.
Session Configuration
Firstly, you should properly configure your PHP session settings. Modify your php.ini file to include secure session configurations. For example, set the session.cookie_secure flag to ensure cookies are only sent over HTTPS.
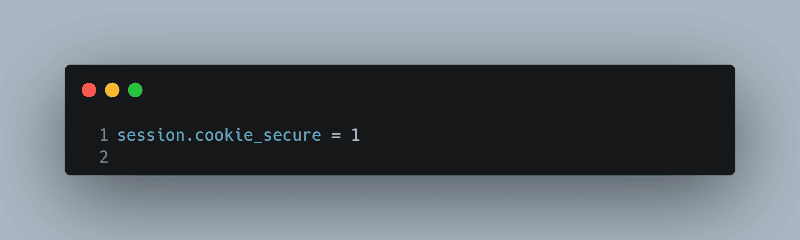
session.cookie_secure = 1
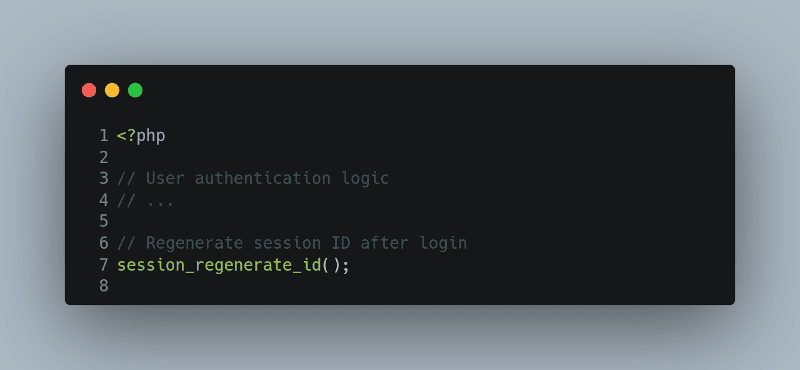
Session ID Regeneration
It’s a good practice to regenerate the session ID after a user logs in to prevent session fixation attacks. This can be easily done with PHP’s `session_regenerate_id()` function:
<?php
// User authentication logic
// …
// Regenerate session ID after login
session_regenerate_id();
Session Timeout
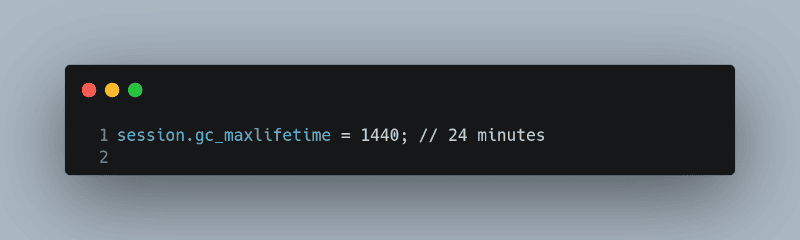
Implement session timeouts to automatically log users out after a period of inactivity. This can be achieved using PHP’s `session.gc_maxlifetime`.
session.gc_maxlifetime = 1440; // 24 minutes
Storing Session Data
Avoid storing sensitive information directly in session variables. If you need to store sensitive data, consider encrypting it before placing it into a session variable and decrypting it after retrieval.
By diligently applying these session management best practices, you can significantly enhance the security posture of your PHP applications, safeguarding both user data and system integrity.
File Upload Security: Limiting Risks Associated with User Uploads
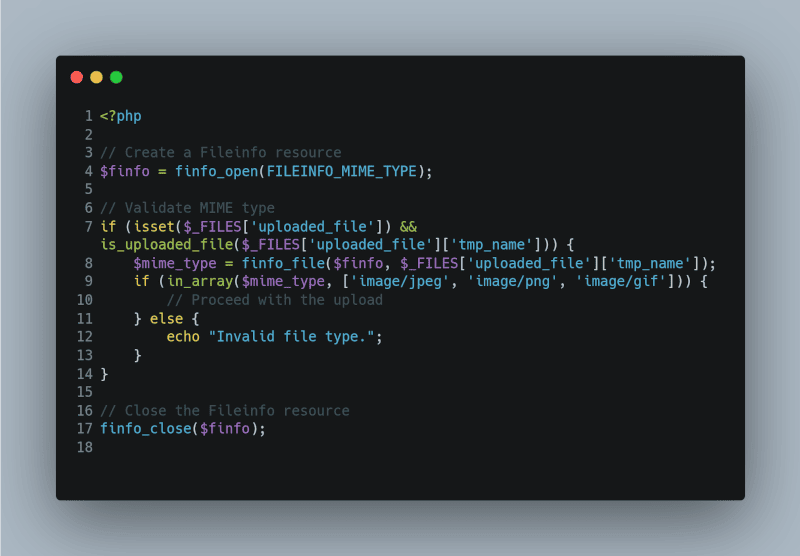
Validate MIME Type
A first step in secure file handling is to validate the MIME type of the file. This goes beyond merely checking the file extension, which can be easily faked. PHP’s `finfo` function can be used to detect the actual MIME type of the file.
<?php
// Create a Fileinfo resource
$finfo = finfo_open(FILEINFO_MIME_TYPE);
// Validate MIME type
if (isset($_FILES[‘uploaded_file’]) && is_uploaded_file($_FILES[‘uploaded_file’][‘tmp_name’])) {
$mime_type = finfo_file($finfo, $_FILES[‘uploaded_file’][‘tmp_name’]);
if (in_array($mime_type, [‘image/jpeg’, ‘image/png’, ‘image/gif’])) {
// Proceed with the upload
} else {
echo “Invalid file type.”;
}
}
// Close the Fileinfo resource
finfo_close($finfo);
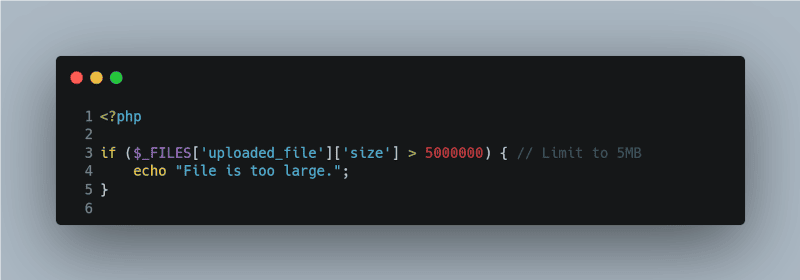
File Size Limitation
Another precaution is to limit the size of the uploaded files. This can prevent a user from uploading very large files that could fill up your server storage.
<?php
if ($_FILES[‘uploaded_file’][‘size’] > 5000000) { // Limit to 5MB
echo “File is too large.”;
}
Server-Side File Renaming
Renaming files on the server after they are uploaded can be a good practice. This can prevent any malicious file from being executed as the attacker would not know the exact file name.
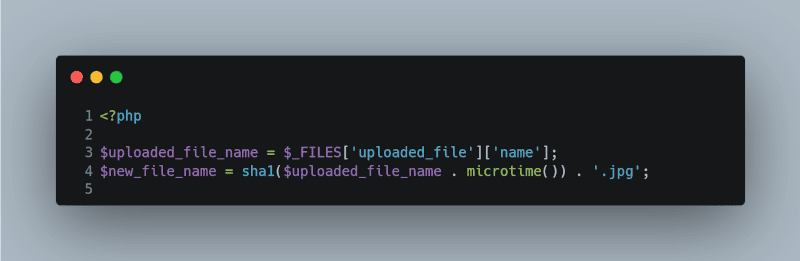
<?php
$uploaded_file_name = $_FILES[‘uploaded_file’][‘name’];
$new_file_name = sha1($uploaded_file_name . microtime()) . ‘.jpg’;
File Upload Location
Always store uploaded files in a secure location. Never store them in a web-accessible directory. Make sure to set proper file permissions on the directory where files are stored.
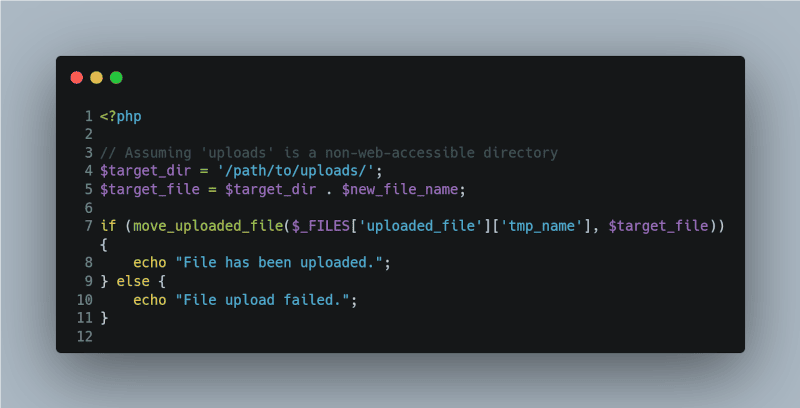
<?php
// Assuming ‘uploads’ is a non-web-accessible directory
$target_dir = ‘/path/to/uploads/’;
$target_file = $target_dir . $new_file_name;
if (move_uploaded_file($_FILES[‘uploaded_file’][‘tmp_name’], $target_file)) {
echo “File has been uploaded.”;
} else {
echo “File upload failed.”;
}
By taking these measures, you can significantly reduce the risks associated with file uploads in PHP applications.
Error Handling: Properly Managing and Logging Errors
Managing errors correctly is critical to the security of any PHP application. Improperly handled errors can expose sensitive information, such as internal file paths, database schema, or configuration settings, to attackers. Here’s how to manage errors in a secure manner.
Turn Off Error Display
Never display errors directly to the user in a production environment as this can expose sensitive information. Instead, log these errors for internal review. In your php.ini file or at the runtime, you can turn off error displaying like so:
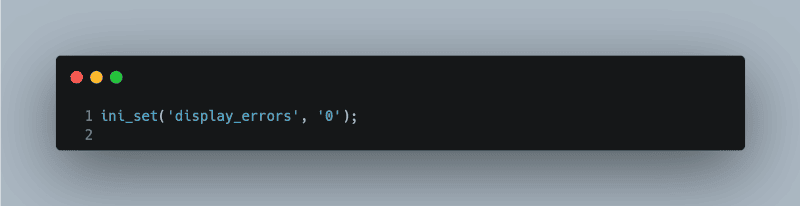
ini_set(‘display_errors’, ‘0’);
Use Custom Error Pages
Always create custom error pages to handle errors gracefully. This ensures that no sensitive system information is disclosed to the user.
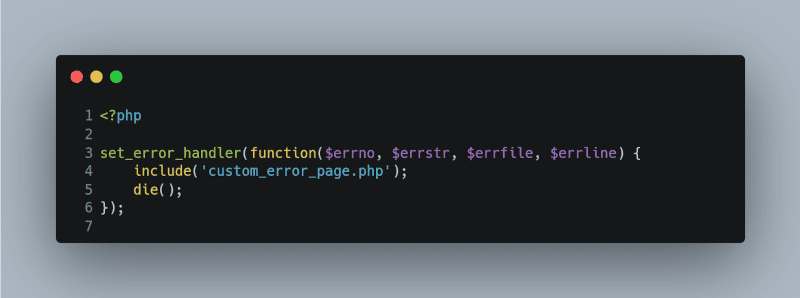
<?php
set_error_handler(function($errno, $errstr, $errfile, $errline) {
include(‘custom_error_page.php’);
die();
});
Log Errors Securely
Errors should be logged securely in a way that allows you to review them and understand what went wrong. But ensure that these logs themselves are secure and not accessible from the web.
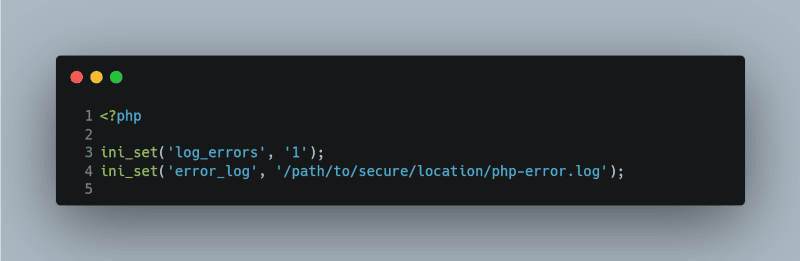
<?php
ini_set(‘log_errors’, ‘1’);
ini_set(‘error_log’, ‘/path/to/secure/location/php-error.log’);
Use Exception Handling
PHP’s try-catch blocks can handle exceptions gracefully, ensuring that errors can be managed in a controlled environment.
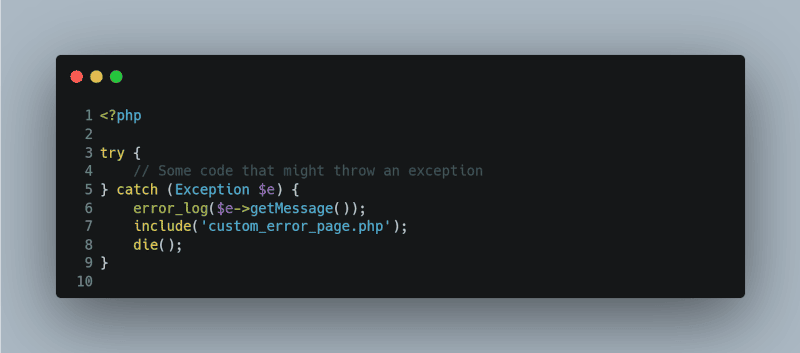
<?php
try {
// Some code that might throw an exception
} catch (Exception $e) {
error_log($e->getMessage());
include(‘custom_error_page.php’);
die();
}
By implementing these error-handling techniques, you add an extra layer of security to your PHP application, ensuring that valuable or sensitive information is not exposed while still allowing for errors to be logged and reviewed for ongoing improvement.
Data Encryption: How to Safely Store and Transmit Data
Data encryption is crucial for protecting sensitive information stored in your database or transmitted over the network. Here are some best practices to ensure your data remains secure.
Use HTTPS for Data Transmission
Always use HTTPS instead of HTTP for transmitting sensitive data. HTTPS ensures that the data between the user’s browser and the server is encrypted and secure.
Hashing Passwords
Never store plain-text passwords in your database. Always use a strong cryptographic hash function like bcrypt to store passwords. PHP’s `password_hash()` and `password_verify()` functions make this simple:
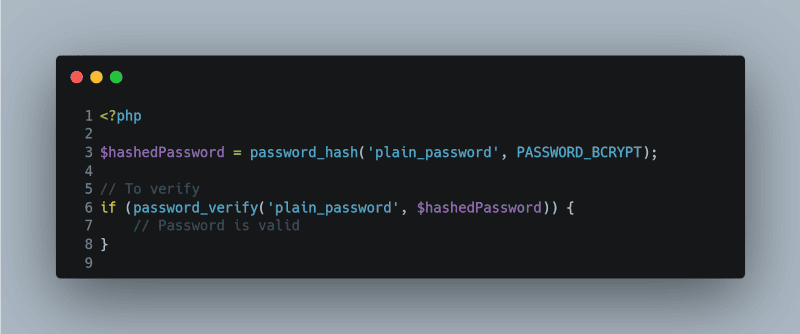
<?php
$hashedPassword = password_hash(‘plain_password’, PASSWORD_BCRYPT);
// To verify
if (password_verify(‘plain_password’, $hashedPassword)) {
// Password is valid
}
Two-Way Encryption
For data that you’ll need to read again, you can use OpenSSL functions to encrypt and decrypt data:
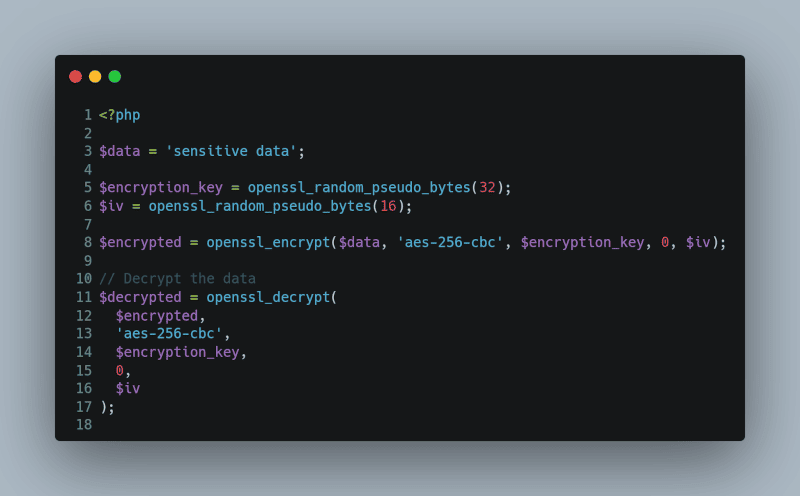
<?php
$data = ‘sensitive data’;
$encryption_key = openssl_random_pseudo_bytes(32);
$iv = openssl_random_pseudo_bytes(16);
$encrypted = openssl_encrypt($data, ‘aes-256-cbc’, $encryption_key, 0, $iv);
// Decrypt the data
$decrypted = openssl_decrypt($encrypted, ‘aes-256-cbc’, $encryption_key, 0, $iv);
Secure Configuration Files
Keep configuration files that contain sensitive information such as database passwords outside of the web root, so they are not publicly accessible.
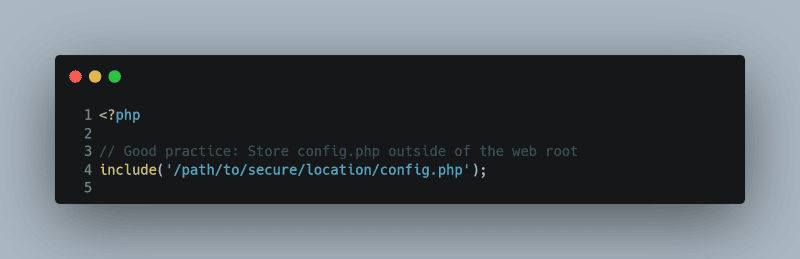
// Good practice: Store config.php outside of the web root
include(‘/path/to/secure/location/config.php’);
Use Prepared Statements
Always use prepared statements for SQL queries to protect against SQL injection attacks:
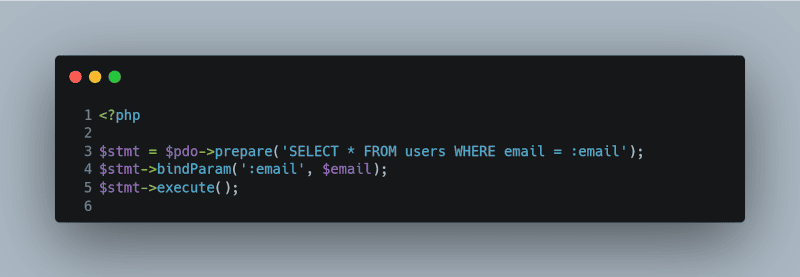
<?php
$stmt = $pdo->prepare(‘SELECT * FROM users WHERE email = :email’);
$stmt->bindParam(‘:email’, $email);
$stmt->execute();
By incorporating these encryption and data storage techniques, you’re adding multiple layers of security to protect sensitive data, both at rest and in transit. This not only protects your application but also instills trust among your users, an invaluable asset for any business.
Role-Based Access Control: Implementing User Permissions
Implementing role-based access control (RBAC) is essential for regulating who has access to different parts of your application. With RBAC, you can specify roles like ‘admin’, ‘editor’, and ‘viewer’, and then assign permissions based on those roles.
Define User Roles Clearly
Start by clearly defining the roles that will exist within your application. Consider what each role should and shouldn’t be able to do.
Implement Middleware
Use middleware to handle role-based authentication checks. This keeps your controllers lean and makes the logic reusable. Here’s an example using PHP:
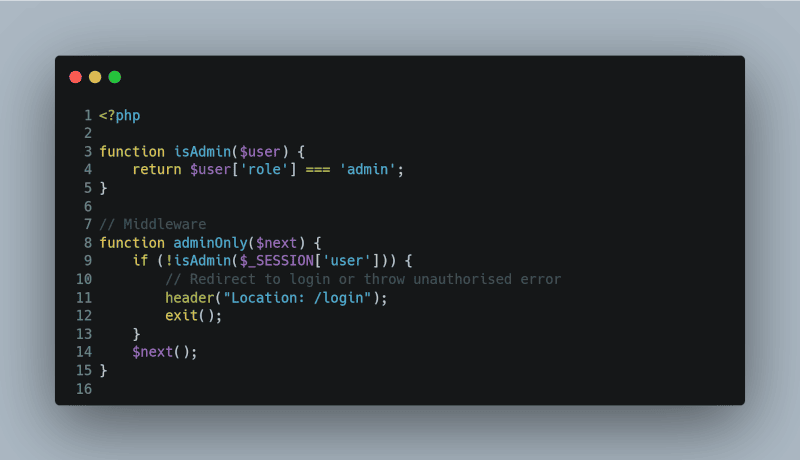
<?php
function isAdmin($user) {
return $user[‘role’] === ‘admin’;
}
// Middleware
function adminOnly($next) {
if (!isAdmin($_SESSION[‘user’])) {
// Redirect to login or throw unauthorised error
header(“Location: /login”);
exit();
}
$next();
}
Restrict Access at the Controller Level
Within your controllers, use the roles assigned to a user to restrict or grant access to specific actions:
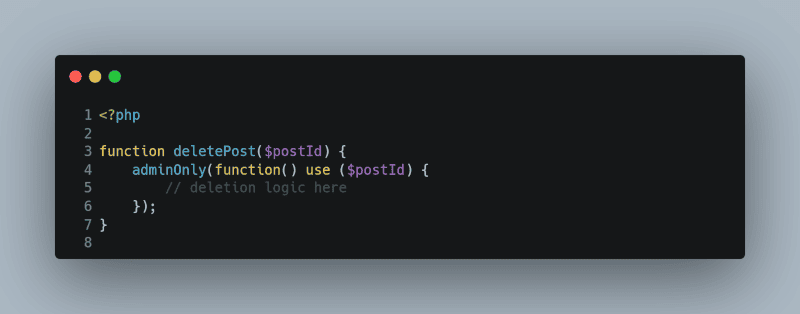
<?php
function deletePost($postId) {
adminOnly(function() use ($postId) {
// deletion logic here
});
}
Keep Role Definitions Flexible
Consider using a permission matrix for roles, which allows you to easily modify what each role can do without having to change code. Store this matrix in a database table or configuration file.
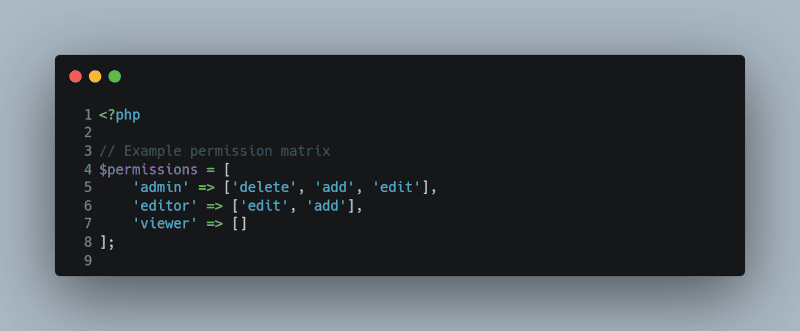
<?php
// Example permission matrix
$permissions = [
‘admin’ => [‘delete’, ‘add’, ‘edit’],
‘editor’ => [‘edit’, ‘add’],
‘viewer’ => []
];
Validate on Frontend and Backend
Never rely solely on client-side validation for access control. While it improves user experience, always validate on the server-side to ensure security.
By implementing role-based access control, you not only improve the security of your application but also make it easier to manage and extend. It’s a scalable way to handle permissions, and it aligns well with the principle of least privilege, granting users only the access they need to perform their tasks.
Cross-Site Request Forgery (CSRF): Understanding and Mitigating Risks
Cross-Site Request Forgery (CSRF) is a type of attack that tricks an end user into executing unwanted actions on a web application in which they’re currently authenticated. If an attacker successfully exploits a CSRF vulnerability, they can perform actions on behalf of an authenticated user without their knowledge, such as changing their email address or password, or making a transaction.
What CSRF Looks Like
A simple example of CSRF would be an attacker embedding an image tag in a forum post like so:
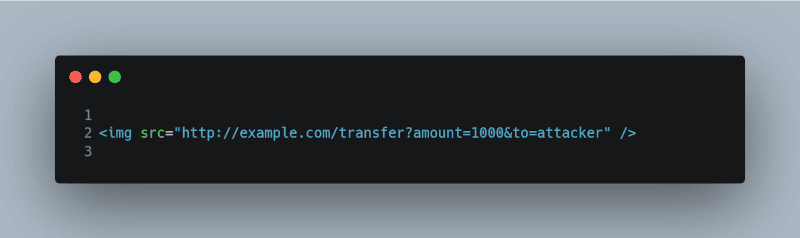
<img src=”http://example.com/transfer?amount=1000&to=attacker” />
If an admin views this post while logged in, the request to transfer funds could be executed without their consent.
Using Anti-CSRF Tokens
One of the most common ways to prevent CSRF attacks is by using anti-CSRF tokens. These are random, unique values associated with the user’s session and are added to forms and URLs that require authenticated actions.
Here’s a simplified example in PHP:
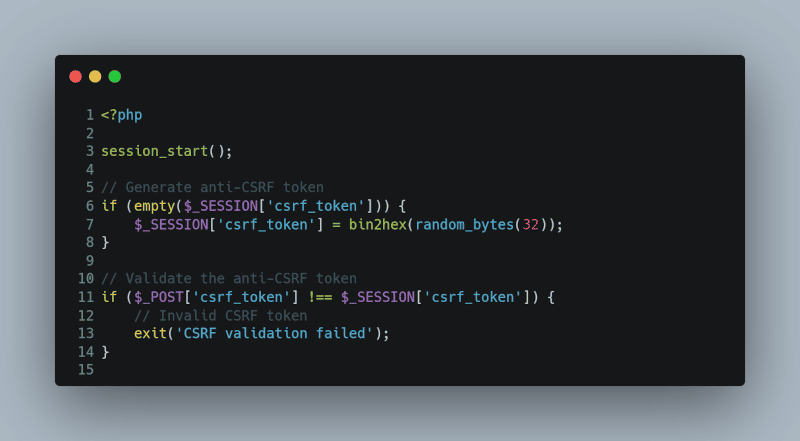
<?php
session_start();
// Generate anti-CSRF token
if (empty($_SESSION[‘csrf_token’])) {
$_SESSION[‘csrf_token’] = bin2hex(random_bytes(32));
}
// Validate the anti-CSRF token
if ($_POST[‘csrf_token’] !== $_SESSION[‘csrf_token’]) {
// Invalid CSRF token
exit(‘CSRF validation failed’);
}
Double-Submit Cookies
Another method is the Double-Submit Cookie technique, where the CSRF token is sent as a cookie and also included as a parameter in the request. The server then validates that both tokens match.
Checking the Origin Header
Some frameworks automatically check the Origin header of incoming requests to ensure they come from a trusted domain. While this is not a substitute for anti-CSRF tokens, it provides an additional layer of security.
Built-in CSRF Protection in Frameworks
Most modern PHP frameworks, like Symfony and Laravel, come with built-in CSRF protection, making it easier to implement secure practices. For instance, in Laravel, you can use the `@csrf` directive to automatically insert CSRF tokens into your forms.
By understanding the risks associated with CSRF and implementing mitigation techniques like anti-CSRF tokens, you can significantly reduce the likelihood of CSRF attacks against your PHP applications.
Final Thoughts on Ongoing Security Maintenance and Monitoring
Securing a PHP application is not a one-time event but an ongoing commitment. Implementing the industry best practices—such as sanitising user input, securing file uploads, proper error handling, data encryption, role-based access control, and CSRF protection—will substantially elevate your application’s security level. However, it’s crucial to remain vigilant and adaptive to emerging security threats.
Regular Security Audits
Conduct regular security audits of your codebase to proactively identify potential vulnerabilities. These audits can be an integral part of your development workflow and can leverage tools like static code analyzers and vulnerability scanners.
Logging and Monitoring
Implement comprehensive logging of security-relevant events and establish real-time monitoring to alert administrators of suspicious activities. This proactive approach aids in the early detection of any security incidents and contributes to thorough forensic analysis.
Software Updates
Keep your PHP version and all associated packages up-to-date. Given that security vulnerabilities are often discovered in libraries and third-party software, update all dependencies promptly to minimise risks.
Employee Training
Regularly train your development and operations teams on the latest security best practices and keep them informed about recent security threats. A well-informed team is far less likely to make security mistakes.
Customer Education
Educate your users about the importance of security best practices, such as using strong, unique passwords and keeping their software up-to-date. User behaviour can often be a security weak link, so empowering your users is key.
Compliance and Regulations
Compliance with the latest data protection and privacy regulations is crucial, especially if you operate across different jurisdictions. Non-compliance can expose you to security risks and legal complications.
A Note from PD Hosting: At PD Hosting, security is not just a feature but a promise. We employ a multi-layered, proactive approach to security, ensuring that we not only adhere to industry best practices but also stay ahead of emerging threats. Our commitment to security is unwavering, and it’s an integral part of our mission to provide reliable, secure, and robust hosting solutions to all our clients.
By taking a proactive, multi-layered approach to security, you can not only protect your PHP applications but also earn the trust and confidence of your users and stakeholders.
—————————————————————————————
Ongoing Security Measures: The Road Ahead
…
At PD Hosting, we consider security to be a continuous journey, not a one-time setup. We constantly monitor and update our security protocols to protect our clients’ digital assets. Our experience in this field positions us well to understand the evolving landscape of cybersecurity threats and to proactively counter them.
I’d like to thank you for the opportunity to discuss these important topics. Security is a shared responsibility, and it’s crucial for developers and hosting providers alike to be vigilant and informed. Thank you for letting me share some insights based on our approach at PD Hosting.