
Short on time? Here’s the best way to make your VPN undetectable in 2025:
- Choose a quality VPN. I recommend ExpressVPN because it’s the most effective provider in making your VPN undetectable.
- Download and install the VPN. Just follow the installation wizard’s instructions, and the whole process won’t take more than 2 minutes.
- Use one of the tips I mentioned here. Changing the VPN’s IP address, using a different protocol, or enabling obfuscation will help you mask your VPN connection.
I always use a VPN to make sure that all of my online activities, including browsing, streaming, and torrenting, are untraceable — thanks to a VPN’s bank-grade encryption, network administrators and internet service providers (ISPs) are unable to see the websites I visit or the files that I download.
However, network administrators and ISPs are still able to detect that I’m using a VPN. But luckily, there are several different ways to make a VPN connection undetectable.
There’s a lot of information about making your VPN undetectable online, but much of it is incorrect. So I spent a few weeks researching this topic. I read dozens of articles, guides, and VPN support articles, talked to many VPN customer support representatives, relied on my own expertise and experience, and conducted multiple tests.
My guide contains useful tips that can actually help you make your VPN undetectable (to a certain extent). In addition, I also recommend the best VPNs for bypassing VPN detection and VPN blocks (ExpressVPN is my #1 pick). Editors' Note: ExpressVPN and this site are in the same ownership group.
Best Ways to Make Your VPN Undetectable in 2025
1. Choose a Quality VPN
The easiest way to avoid VPN detectors and VPN blocks is to just use a VPN proven to be undetectable. For that, you need a VPN that refreshes its IP addresses very often, hides VPN traffic, and provides overall excellent security and privacy features.
After running dozens of tests, I found that ExpressVPN is the best option for surfing the web undetected — here’s why:
- It constantly refreshes its server IP addresses. I ran 10+ leak tests while connected to its New York server, and I always had a different IP address. This is also the reason why it consistently works with top streaming sites and in restrictive countries.
- It supports obfuscation on all servers. This is a security feature that hides your VPN traffic, making it resemble normal internet traffic. It allows ExpressVPN to bypass VPN traffic blocks in restrictive countries.
- It has ShuffleIP. This is a security feature that makes sure you use a different IP address every time you connect to a new website. This provides enhanced privacy, and it also makes it harder for sites to block your VPN connection.
- It supports Tor over VPN connections. This makes your VPN’s IP address even harder to detect.
- It provides high-end privacy. It does this via an audited no-logs policy and advanced security features like full leak protection.
Quick summary of the best VPNs for avoiding VPN blockers in 2025:
- 🥇1. ExpressVPN — Best overall VPN for avoiding VPN blockers (works 100% of the time).
- 🥈2. Private Internet Access — Privacy-focused VPN for avoiding VPN blockers (open-source apps).
- 🥉3. PrivateVPN — Beginner-friendly VPN that gets around VPN blocks (has obfuscation).
2. Change the VPN Protocol

Restrictive countries and network admins can stop you from using certain VPN protocols if they block the ports used by those protocols. They can also use deep packet inspection (DPI) to detect and block certain VPN protocols. The easiest way to overcome those restrictions is to change the VPN protocol. Keep in mind that getting around these restrictions is illegal in some places, so make sure you do your research before doing so in your current location.
If you’re dealing with port blocking, I recommend using OpenVPN or WireGuard. If their default ports are blocked, you can manually switch to a different port. Both WireGuard and OpenVPN support tons of ports. ExpressVPN supports OpenVPN and its proprietary protocol, called Lightway, is essentially an improvement on WireGuard. It’s also one of the top VPNs that configures these protocols to automatically work with ports that are hard to block, so you don’t need to manually pick a port (which is very convenient if you’re a beginner).
For DPI, the easiest fix is to use a VPN protocol that hides your VPN traffic. Many top VPNs provide such options — for example, ExpressVPN has Lightway and VyprVPN has Chameleon.
3. Use Obfuscation Features

Obfuscation is a VPN feature that encapsulates VPN traffic in an extra layer of encryption to make it look like regular internet traffic. Obfuscation is the best way to bypass DPI detection and blocks (only if it’s not illegal in your location).
VPNs usually support obfuscation via the OpenVPN protocol, while some have proprietary protocols that come with obfuscation. Most providers have a built-in obfuscation feature — once you enable it, it will obfuscate VPN traffic via dedicated servers (or even all servers).
I personally like ExpressVPN’s obfuscation the most. It supports obfuscation on all servers via its proprietary Lightway protocol, and via the OpenVPN protocol. And you don’t need to turn the obfuscation on since it’s always enabled, which is really convenient. Also, ExpressVPN is one of the few top VPNs that work in restrictive countries like China (per its customer support reps) — and China’s application of DPI is arguably among the most extensive and sophisticated in the world.
4. Use TCP Port 443

If most VPN-related ports are blocked, I suggest switching to TCP port 443, the same port used by HTTPS traffic, which accounts for almost all internet traffic. It’s extremely unlikely that an ISP or network admin would block this port, as it would mean blocking access to any website that uses HTTPS (like Facebook, Google, Twitter, YouTube, etc.).
Only some VPN protocols are able to use TCP port 443:
- OpenVPN. This is a very popular and secure protocol. Some VPN providers, like Private Internet Access allow you to pick TCP port 443 when you select OpenVPN. Others, like
ExpressVPN , configure OpenVPN to automatically use TCP port 443, which is very convenient. - SSTP. This protocol uses TCP port 443 by default, but only a few VPN providers offer access to it.
- SoftEther. Very few VPN services use this protocol because it’s difficult to integrate it into the VPN client.
5. Use Tor Over VPN
Tor is a privacy network that lets you access the dark web. Tor also routes your traffic through multiple servers, changing your IP address and encrypting your traffic several times. Tor is free to use — you only need to download and install the Tor browser to access the Tor Network.
You can tunnel a Tor connection over a VPN connection to prevent internet and dark web sites from detecting your VPN IP address and hide your VPN connection behind several layers of Tor encryption. Basically, your connection will look like this:
You → VPN → Tor Server #1 → Tor Server #2 → Tor Server #3 → Internet or Dark Web
Pretty much all top VPNs support Tor over VPN connections, but I like ExpressVPN the most because it has really fast speeds (Tor over VPN connections are usually pretty slow). I also think NordVPN is a good pick because it has Onion Over VPN servers that automatically send your traffic through the Tor network, meaning you don’t need to download and use the Tor browser to use the Tor network.
6. Change the VPN’s IP Address
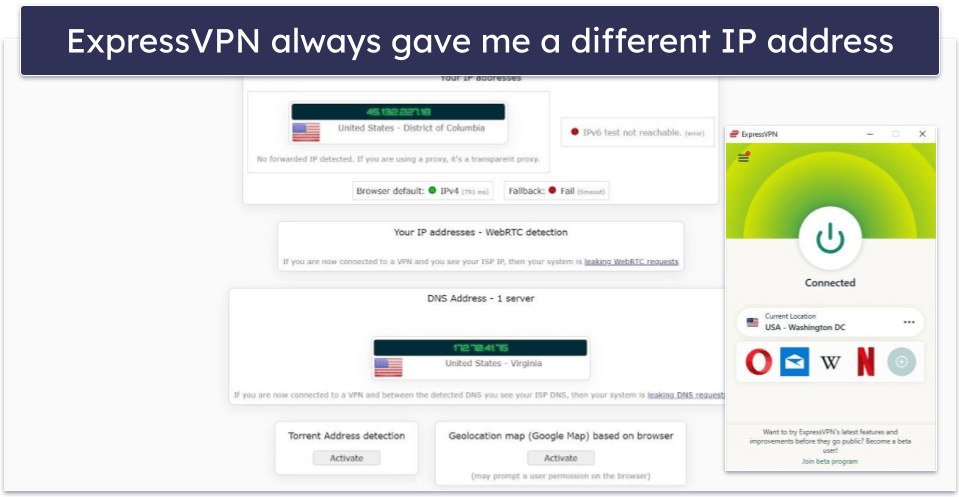
If a network admin blocked the VPN’s IP address, refresh the VPN server’s IP address to bypass that issue. The simplest way to do that is to reconnect to the VPN server or connect to a different VPN server.
ExpressVPN automatically refreshes your IP addresses very often — when I ran tests while connected to the same server, I always got a different IP address. The provider also has ShuffleIP, which makes sure you use a different VPN IP for each new site you access. That provides enhanced privacy by making it harder for ad trackers to monitor your online preferences, and it also makes it harder for sites to block your VPN IP.
Some VPNs have built-in features that regularly refresh the IP address in the background — for example, Surfshark has IP Rotator, a tool that changes your VPN IP address without disconnecting you from the VPN server, which you have to turn on in the settings.
7. Use a GPS-Spoofing Feature or App
This tip is useful for mobile users, as many mobile apps (especially streaming apps) might use your device’s GPS data to check your location. This means the app could accurately tell what your real location is even though you’re connected to a VPN — if this happens, the app might then block your VPN connection.
The solution is to spoof your device’s GPS data and make it match the location of the VPN server you’re connected to. This can be done via GPS-spoofing apps, though it’s much easier to do on Android since such apps are available on the Google Play store.
On iOS, you need to jailbreak your device and use GPS-spoofing apps from unofficial app stores — this could expose you to malware, and it might cause your device to malfunction. There is an alternative to jailbreaking your iOS device, but it’s not convenient. You’d need to set up a GPS-spoofing app on your laptop or desktop, connect your iOS device to the computer and then use the app on your desktop or laptop to change the GPS data on your smartphone.
If you’re an Android user and would like to spoof your device’s GPS data, I recommend trying Surfshark or

8. Use Mobile Data
Businesses and learning institutions often implement strict anti-VPN policies on the company/school’s network. If you’re caught using one, you could get in trouble.
In this case, the best way to make your VPN usage undetectable is to use your mobile data. That way, you use your telecom provider’s network instead of your company/school’s network.
9. Use Shadowsocks

Shadowsocks is an open-source encrypted proxy, which you can use to connect to VPN servers. If you do that, Shadowsocks will encrypt your connection to the VPN server, making it much harder for someone to detect and block it.
Shadowsocks requires a manual setup, but it’s pretty simple to use. However, you need to use it with a VPN that supports Shadowsocks connections to its servers. The VPN also has to support manual port selection, since you need to pick a server port while setting up Shadowsocks.
I personally recommend using a VPN that has built-in support for Shadowsocks (like Private Internet Access) instead because it’s much more convenient.
Editors' Note: Intego, Private Internet Access, CyberGhost and ExpressVPN are owned by Kape Technologies, our parent company
Why Should You Make Your VPN Undetectable?
- Bypass VPN blocks — Restrictive countries like China, Iran, and Indonesia often employ state-of-the-art methods to detect and block VPN connections. While most of these countries don’t specifically make it illegal to use a VPN to get around these restrictions, some legally ban them so it’s important to check all local rules and regulations before using a VPN. Also, learning institutions and workplaces might use firewalls to block VPNs.
- Get more privacy — When you connect to a VPN, your ISP is aware of the connection (but the VPN’s encryption prevents your ISP from seeing your internet behavior). Also, websites can detect VPN IP addresses. Some people simply don’t want their ISPs or the sites they visit to know they’re using a VPN.
What Are VPN Blockers & Why Are They Used?
VPN blockers are services or tools that detect and block VPN connections. Governments, ISPs, network admins, and websites use VPN blockers — and here’s why:
Enforce Government Censorship
Restrictive countries often block access to popular sites, including social media sites, news sites, and platforms like Google and YouTube. These countries know that their citizens can use a VPN to circumvent government firewalls and access a free and open internet, so they use sophisticated technology to detect and block VPN connections. Note that in some of these countries, using a VPN to get around the firewall is illegal, so it’s important to do your research before doing so.
Enforce a School/Workplace Policy
Many schools, universities, and businesses use firewalls to stop students/employees from accessing certain sites. Since students/employees can use a VPN to bypass the firewall, school and workplace network admins block VPN connections.
Honor Copyright and Licensing Agreements
Streaming platforms display different titles depending on which country you’re in — this is all due to the licensing agreements they signed with copyright holders. Basically, if a site doesn’t have the licensing rights to show a specific title in a certain country, it can’t legally broadcast it there.
Streaming sites detect and block VPNs because they allow people to bypass geo-restrictions (a type of content protection). If the sites were to ignore VPN connections, it could be a breach of the licensing agreements they signed.
Avoid Legal Issues
Some ISPs worry that their customers might use VPNs to illegally torrent copyrighted content. To avoid facing any potential legal repercussions, they throttle or block VPN connections on their networks.
And certain websites might also block VPNs to avoid legal issues — for example, gambling sites block VPNs to prevent people from countries where gambling is illegal from using their platforms. Also, payment processing sites might block VPN connections as a fraud prevention method (they worry criminals use VPNs to launder money).
Different Types of VPN Blockers
Here are the main VPN blocking methods:
IP Blocks
When using a VPN, websites only see the IP address of the VPN server you’re connected to. If a site blocks that IP address, you won’t be able to access the site through it.
Many streaming platforms use IP blocks to prevent VPN users from accessing geo-blocked content. To do this, they often source VPN and proxy IP databases from services like IP2Location. Subsequently, these websites employ automated scripts designed to detect and block VPN IP addresses that want to establish connections with their platforms. What’s more, network administrators, internet service providers (ISPs), and governments with stringent policies employ firewalls to impede connections from VPN IP addresses, further limiting access to these platforms.
Port Blocking
Ports are numbers assigned to network protocols used for online communication. Each VPN protocol uses different ports to access the web — for example, OpenVPN uses UDP port 1194 by default. Network admins and ISPs can block certain ports to prevent you from using a specific VPN protocol.
Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) searches for indications and signatures in your internet traffic that suggest you’re using a VPN protocol. If a VPN is identified, DPI has the capability to either obstruct it or slow it down to the point of being ineffective, a strategy referred to as Quality of Service filtering. Countries that impose VPN restrictions, such as China, use DPI to identify and hinder OpenVPN connections.
Can Decoy Traffic Make Your VPN Undetectable?
Not exactly. Decoy traffic is meant to make it harder for third parties to detect specific online activities when someone is connected to a VPN. That kind of detection could actually be achieved via traffic correlation attacks, which use data volume (how much data you download and upload) to identify certain web apps and websites.
For example, let’s say you use a VPN to upload torrents or post on social media. Even though your ISP couldn’t see that you’re interacting with torrents and social media sites, it could still detect your upload volume. If it detects a lot of upload spikes, that could be a sign of torrenting or social media posting. While this is very hard to achieve for the ISP, it’s not impossible.
That’s where decoy traffic comes into play. Using decoy traffic basically means you’re generating “fake” traffic between your device and the VPN server. This is achieved by uploading and downloading random data at specific intervals, which should make it harder for third parties to use traffic correlation attacks against you. Just remember this will make it harder for someone to detect specific online activities when you’re using the VPN — it won’t make it harder for someone to detect your VPN connection.
If you’re interested in using decoy traffic with a VPN, try Windscribe, since it has this feature on its Android app. Just keep in mind that using it will significantly increase your data usage, and it will also throttle your speeds a bit (this is done to make it even harder for third parties to single out specific web activities).

Can You Use Dedicated IPs to Make Your VPN Harder to Detect?
I have seen a lot of online sources claim that using a dedicated IP address (an IP that’s only assigned to you) will make your VPN connection harder to detect. But this is actually incorrect, and I think many people believe this because they think that streaming sites don’t block dedicated VPN IP addresses.
But streaming services actually block dedicated VPN IPs just as easily as they block shared VPN IPs. In fact, most VPNs with dedicated IPs advise against using their dedicated IPs for streaming — if a streaming site blocks the dedicated IP you’re using, you’ll need to pay for a new one.
Keep in mind that most dedicated VPN IPs come from data centers, and data center IPs are usually added to databases by proxy detection services. Streaming sites use these databases to block VPNs.
You could make it harder for streaming sites to detect your dedicated IP by making sure it’s a residential IP, which means it comes from an ISP instead of a data center. But even a residential dedicated IP could still be detected and blocked. If you really want to try one out, check out TorGuard.

I personally only recommend using a dedicated IP to access websites that mainly block shared IPs, like bank sites, and to avoid seeing too many reCAPTCHAs on search engines.
Can I Avoid Detection by Setting Up My Own VPN Server?
Personally, I don’t think so. Setting up your own VPN usually means renting a virtual server that you configure to act as a VPN server. You then connect to the virtual server and use it to surf the web.
But you run into the same issue you do with dedicated IPs — streaming sites can still detect and block your virtual server IP address. It comes from a data center, after all. If that happens, you’ll need to request a new IP, and the hosting provider will likely charge you for that.
Plus, the whole process is very time-consuming, and you also need to be really tech-savvy to handle it. After all, you need to set up the virtual server, and then configure it to use a VPN protocol.
And you of course need to pay for a virtual server. Virtual servers running Windows are easier to use, but their prices start at around $10–$12 per month. You get prices under $10 per month if you get a virtual server running Linux, but it’s more difficult to configure.
Considering all of that, you’d be much better off just getting a premium VPN that’s affordable, easy to use, and can bypass pretty much any type of detection — like ExpressVPN, for example, whose prices start at $4.99 / month.
Editors' Note: ExpressVPN and this site are in the same ownership group.
Does VPN Over Tor Make Your VPN undetectable?
Not really. VPN over Tor means you tunnel your VPN connection over the Tor network (a privacy network that hides your IP address and encrypts your traffic multiple times by sending it through at least 3 servers).
Basically, your connection will look like this:
You → Tor Server #1 → Tor Server #2 → Tor Server #3 → VPN → Internet
A VPN over Tor connection will prevent ISPs and network admins from seeing that you’re connecting to a VPN’s IP address — but they’ll still know you’re connecting to a Tor IP address, and they’ll be able to easily block it (Tor doesn’t refresh its IP addresses very often). And VPN over Tor connections aren’t safe, since Tor can sometimes leak your IP address and malicious actors can operate their own Tor servers.
I recommend Tor over VPN connections instead because they hide your VPN’s IP address from normal internet sites and dark web sites and are also much safer — if Tor suffers a leak, only the VPN’s IP address is exposed and your IP address remains hidden. Most top VPNs support Tor over VPN on their servers.
Frequently Asked Questions
Can I use a free VPN to circumvent detection?
I doubt it — free VPNs rarely refresh their IP addresses, so it’s easy for sites and network admins to block their servers. What’s more, most free VPNs don’t provide access to obfuscation or protocols that can use multiple ports (like OpenVPN and WireGuard). Also, many free VPNs lack essential VPN security features like a kill switch or a no-logs policy.
I strongly advise getting a paid premium VPN like ExpressVPN instead — it regularly refreshes its IP addresses, has good streaming support, works in restrictive countries, has Tor over VPN support, and provides access to high-end security features.
Does changing DNS settings make a VPN harder to detect?
No — configuring your device to use third-party DNS settings, like Google Public DNS or Cloudflare DNS, won’t make your VPN connection undetectable. If you do that, it just means your DNS queries (what site you connect to) will go through the third parties’ DNS servers instead of your VPN’s DNS servers. VPNs only recommend doing this when dealing with VPN connectivity issues.
As long as you use a secure VPN with strong DNS leak protection (like ExpressVPN), you don’t need to worry about DNS security leaks. If the VPN has DNS leak protection, it means it runs its own encrypted DNS servers.
Will a double VPN connection make a VPN undetectable?
Not really. A double VPN connection sends your traffic through 2 VPN servers instead of 1 server — while that hides the IP address of the 1st VPN server, it’s still possible to detect the IP address of the 2nd VPN server. Plus, a double VPN connection won’t prevent network admins or ISPs from detecting VPN traffic.
I recommend using double VPN when you need an extra layer of encryption to secure your data. Surfshark has a very good double VPN feature that lets you pick the entry and exit servers (most VPNs with double VPN support don’t let you do that).
Can you use a proxy to make your VPN undetectable?
Probably not. Some online sources say you can use a proxy to hide your VPN IP — basically, you first connect to the VPN and then the proxy. After that, you use the proxy’s IP address to surf the web. But this likely won’t work due to potential connectivity issues between the VPN and the proxy. It’s much better to just try the tips mentioned here instead.
Does obfuscation stop streaming sites from detecting VPNs?
No, obfuscation can only help you get around Deep Packet Inspection (DPI), which detects and blocks VPN traffic. Obfuscation should generally be used in restrictive countries or if you want to prevent network admins or ISPs from tracking your VPN traffic. ExpressVPN is the best in the industry because it supports obfuscation on all of its servers and all VPN protocols. It’s also one of the only VPNs that work consistently in China, where the government applies DPI extensively to monitor and restrict internet usage.
Are peer-to-peer (P2P) VPNs harder to detect?
Not really. People probably get this impression because, with P2P VPNs, you access the web via other VPN users’ IP addresses (and they browse the web via your IP). Due to this, people assume that it will be harder for sites to detect and block your VPN IP.
But I already mentioned how even residential IPs can be blocked — not to mention that P2P VPNs are risky to use, as other users could use your IP to engage in illegal activities (like downloading copyrighted content).
