
Led by Anurag Sen, the SafetyDetectives security team discovered a misconfigured server belonging to an unknown entity that leaked data for potentially millions of people.
The ElasticSearch server contained millions of logs of personal data — information that belongs to Russians, Ukrainians and Kazakhs applying for “microloans.” Though the identity of the server owner was unclear, several microloan companies had customer logs included in the server.
Who Owns the Server?
We do not know the entity that operates the ElasticSearch server in question. We did, at one stage, determine the company name of the server owner. However, this entity’s website is no longer in operation and we cannot find any further information about the company.
There were several websites with logs of microloans data on the server. Interestingly, the exposed websites are not financial services, such as banks or loan companies. Rather, they are third parties that act as intermediaries between customers and loan companies.
Numerous entries within the server’s logs are written in Russian and much of the data seems to belong to users from Russia and its surrounding countries, including Ukraine. As such, the ElasticSearch server probably belongs to a Russian entity.
What was Exposed?
The anonymous ElasticSearch server was left unencrypted and unsecured without any authentication controls in place. As a result, the misconfigured server leaked over 870 million records, equating to more than 147 GB of data.
The server contained logs of data related to various microloan companies. There are over 10 million records of user PII on the server — information that belongs to people who applied for microloans with the companies featured on the server.
Altogether, several forms of user PII and sensitive user data were exposed on the server’s logs. Some of this information is from users’ “internal passports*”, while there are various other forms of user data exposed on the open ElasticSearch server.
Internal Passport Details
*In Russia and Ukraine, internal passports work like national IDs that are designed for use within borders.
The server’s logs contained “internal passport” details which revealed personal and sensitive user information:
- Full names, incl. First name, last names, and patronymic names
- Genders
- Birth dates
- Birthplaces
- Marital statuses
- Physical addresses with city & region details
- Other internal passport details, incl. Passport number, serial number, expiry date, and issued by
In some cases, information like names, cities, addresses, and “issued by” locations were written in Cyrillic. In other instances, this information was decoded into special symbols. The Cyrillic script is a writing system used in parts of Europe and Asia.
You can see evidence of internal passport details in the screenshot below.
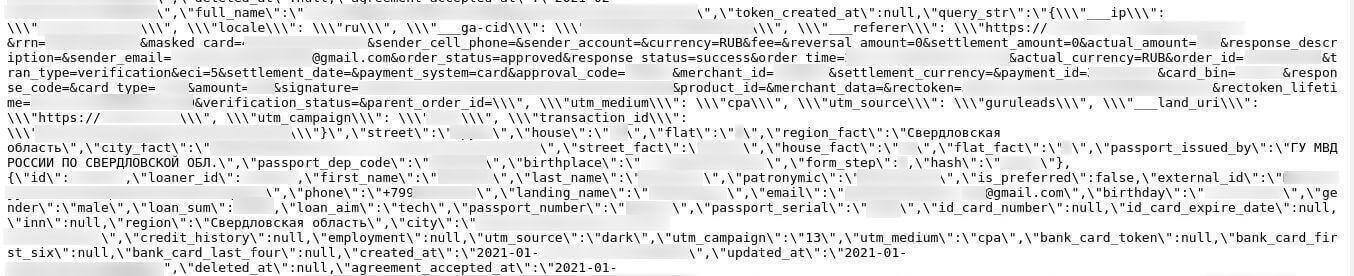
Internal passport info exposed on the ElasticSearch
Various User Data
Other forms of user PII and sensitive user data was featured alongside internal passport details in the ElasticSearch server’s logs:
- Card details, incl. Card number, expiry date, cardholder name, CVV (in some cases)
- Mobile numbers
- Email addresses
- Employment status’
- Salary
- Education information
- Child count
- Login OTP SMS codes*
- Loan details
- INN, i.e. tax identification numbers
*Note: These are one-time (often numeric) passwords that are sent to a user’s phone to help verify their identity during the login process.
You can see evidence of the user information exposed in the logs below.

Card details (including CVV) were found on the server

The employment status of users also leaked
Russian, Ukrainian, and Kazakh users were exposed in the open ElasticSearch server’s logs. The majority of the server’s logs related to Russian users. The passport numbers we found related primarily to Russian citizens, while INNs (tax identification numbers) belonged to Ukrainian citizens. You can see evidence of a Ukrainian user’s INN below.
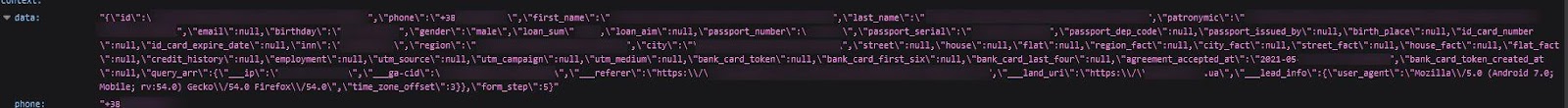
An INN belonging to a user from Kyiv, Ukraine [written in unicode]
You can see a full breakdown of the microloans data exposure in the table below.
The SafetyDetectives security team discovered the ElasticSearch incident while randomly checking IP addresses at a particular port.
The misconfigured ElasticSearch server was found on December 5th, 2021. We believe the server has been exposed on the internet since this day.
After we found the anonymous ElasticSearch server, we contacted the Russian CERT on December 14th, 2021. Russian CERT replied to our message, informing us that the incident is not under their jurisdiction because the server has a Netherlands IP address. We contacted the Dutch CERT on December 30th, 2021, who could not help us either, and on January 9th, 2022, we contacted the server’s hosting company. On January 13th, 2022, the hosting company replied to our message and we responsibly disclosed the data breach. The anonymous ElasticSearch server was secured on the same day.
Data Breach Impact
The microloan applicants with data exposed on the ElasticSearch server could face various impacts because of this data exposure, while the server owner could come under the scrutiny of data protection authorities.
Impact on Exposed Users
We do not and cannot know whether the anonymous ElasticSearch server’s content has been accessed by any hacker or malicious party. The server was left unsecured and unencrypted, which means anyone who found the server’s IP address could’ve accessed its logs.
If any bad actors have read or downloaded users’ data stored on the ElasticSearch, exposed users could experience various forms of cybercrime.
Exposed users could experience scams, phishing attempts, and spam marketing messages if bad actors have found the names, addresses, email addresses, and mobile phone numbers on the server.
In scams and phishing attempts, attackers could contact users via email or phone while masquerading as a representative of a microloan broker. Attackers could refer to users by name and reference various PIIs and loan details to build trust with the victim.
Hackers could extort victims for money with a scam. For example, a hacker could convince a victim to pay a fake loan fee.
In a phishing attempt, attackers could leverage trust to extract further information from the victim or convince the victim to click a malicious link. Malicious links can infect the targeted user’s device with malware once clicked.
Companies and other entities could acquire the server’s content to send unsolicited spam marketing messages to exposed users.
Identity fraud is another possibility with personal information and passport details leaked on the server. Cybercriminals could use these details to assume the identity of the victim. Attackers could open bank accounts, apply for loans, and obtain genuine documents in the victim’s name.
In particular, the open ElasticSearch’s content could allow cybercriminals to carry out microloans identity fraud, which is currently a common issue in Russia. People involved in this malpractice use stolen passport details to take out fraudulent microloans in other peoples’ names.
Exposed users are also at risk of credit card fraud given the extensive credit card details stored in the ElasticSearch server’s logs.
There were full credit card numbers, expiry dates, card security codes, and cardholder names on the server. A hacker could potentially use these details to make purchases in the victim’s name or drain the victim’s bank account of funds.
Preventing Data Exposure
What can we do to protect our data and minimize the risk of cybercrime?
Here are a few tips to prevent data exposure:
- Don’t give your personal data to any company, organization, or person unless you trust that entity 100%.
- Only visit websites that have a secure domain name (i.e. domains with a “https” and/or closed lock symbol at the beginning).
- Be extra careful when providing your most sensitive forms of data, such as your social security number.
- Create secure passwords that contain a mixture of letters, numbers, and symbols. Update your passwords regularly.
- Don’t click a link online unless you’re completely sure it’s from a legitimate source. Malicious links can be found in emails, messages, or on phishing websites that are masquerading as legitimate domains.
- Edit your privacy settings on social media so that your content and personal information are only visible to friends and trusted users.
- Avoid displaying or typing highly sensitive data (such as credit card numbers or passwords) when you’re using a public or unsecured WiFi network.
- Educate yourself about the risks of cybercrime, the importance of data protection, and the steps you can take to avoid phishing attacks and malware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach affecting the multinational security firm Securitas that exposed over 1 million files related to Airports and their employees.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.