
Updated on: September 25, 2024
The SafetyDetectives cybersecurity team has discovered a vulnerability affecting baby monitors, provoked by their misapplication/misconfiguration, which provides potentially harmful parties with unauthorized access to each camera’s video stream.
In mid-December 2020, our cybersecurity team identified numerous baby monitors that are amongst the RTSP devices that do not require authentication for unknown parties to connect.
‘RTSP’ (Real-Time Streaming Protocol) is a set of procedures used by various cameras to control their streaming media. Many baby monitors use RTSP, and it’s important to highlight that other cameras using RTSP (like CCTV cameras) could also be unsecured due to misconfiguration, and unsafe to use for some applications.
Whilst this means that potentially harmful individuals could be able to access private images of your children, their bedrooms, and possessions, this specific vulnerability is also concerning with regards to daycare centers – which are commonly known to stream video from inside kindergarten for onlooking parents and guardians.
If you monitor your children through a live-feed camera this is worrying information. We are here to outline all of the potential dangers, how these unauthorized connections occur, and what you can do to prevent people from accessing your baby monitors or other RTSP cameras.
Who is at risk?
If your baby monitor or any RTSP camera does not require parties to enter a password each time they connect to the video stream, the images shown on that stream are potentially unsecured, and therefore accessible to anyone.
Similarly, if your child attends a daycare center that live streams images to parents through the use of baby monitors, or other cameras using RTSP, these images could be unsecured and accessible to any unknown and possibly harmful person.

Snoopers could be accessing images of your children.

Many daycare centers stream their interior monitors, which could be unsecured.
The SafetyDetectives cybersecurity team has determined a number of specific RTSP devices that are vulnerable to misuse and misconfiguration, resulting in a potentially unsecured and unsafe video stream. We have also provided a (non-exhaustive) list of some countries in which we have found this kind of data exposure to take place.
Models/Devices
The following devices could provide unauthorized access to their video stream if they are used as baby monitors. These devices are commonly misused and can become unsecured if exposed to the internet, or if they are configured without password protection. There could be more devices like this not listed in our table.
*Note: the issue doesn’t arise from a malfunction of the device, it occurs due to a misconfiguration by the owner/company.
Countries
The following countries are some of the locations we’ve found to be vulnerable to this kind of data exposure.
This investigation was fueled by the curiosity of our SafetyDetectives security team. We asked ourselves the question: “What types of devices do people often fail to configure properly?”
Initial research was carried out through the search engine ‘Shodan’, and after a short while it became clear that baby monitors are a commonly misused and mis-sold product.
While there are other misused devices, we chose to focus our research on baby monitors. The risk involved with misusing a baby monitor is greater than with many other products. Not only because of the sensitive nature of their content, but also because predators are actively searching for this type of content.
From here, our team was able to identify unsecured devices either through their ‘server header,’ or their onscreen overlay that details the particular brand. A server header is a strip of information provided with RTSP that details numerous factors, including the device type. The server header can be seen in the below example:

Regardless of whether your country or device is outlined here, you should check that your camera has an adequate level of security, as you may still be at risk.
How do I know if my kids are being exposed?
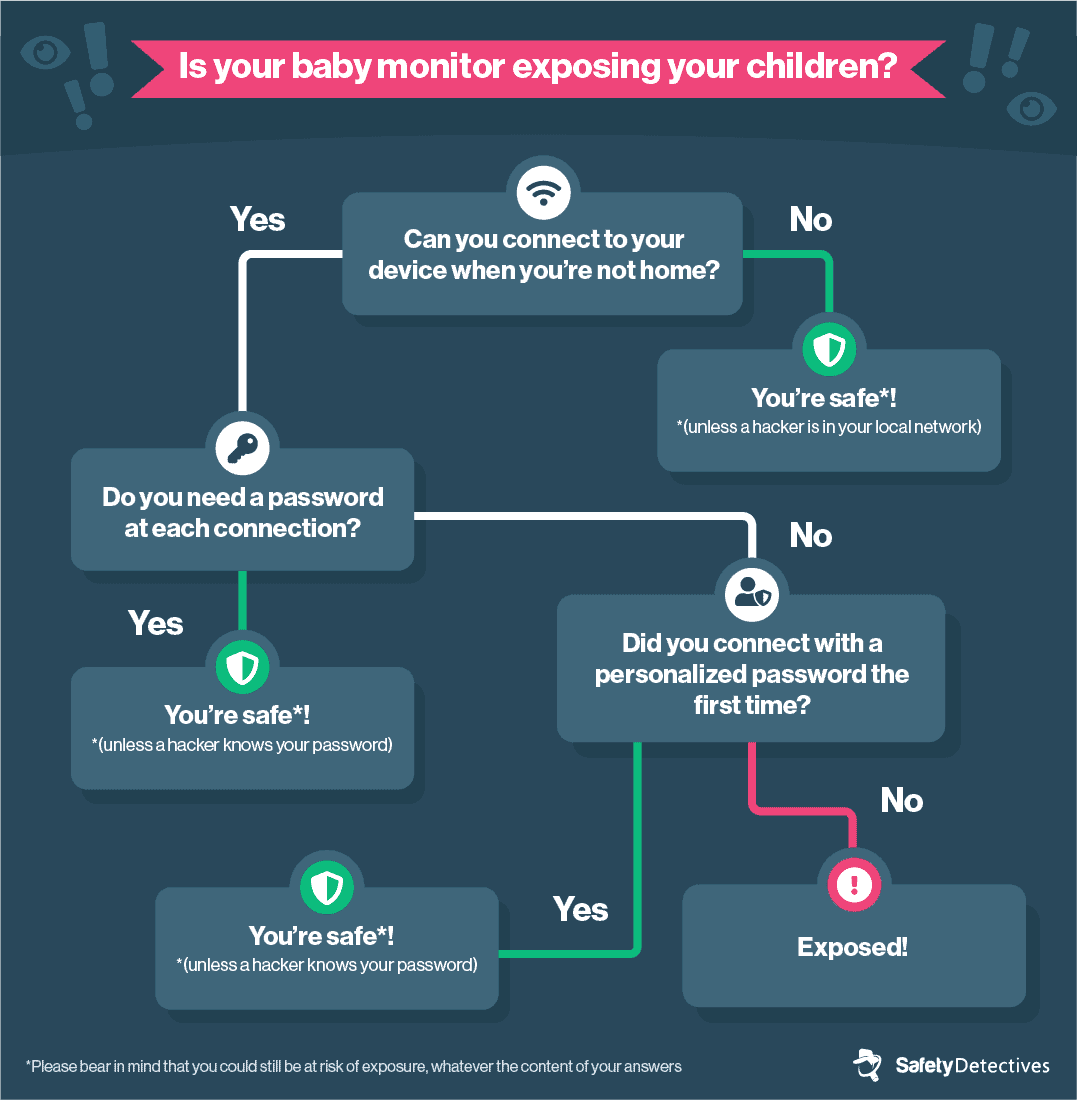
We’ve created a step-by-step visual guide to help you figure out whether your baby monitor, or RTSP device, could be exposing your children. Simply answer each question honestly and follow every instruction provided.
While there could still be the risk of exposure, whatever your answer for each section, this guide is essentially the easiest way to determine whether your baby monitor stream is unsecured, and therefore exposed.
Following this guide, there are some additional steps you can take to double-check the security of your monitors. This is for tech-friendly users, who feel comfortable accessing their router’s settings.
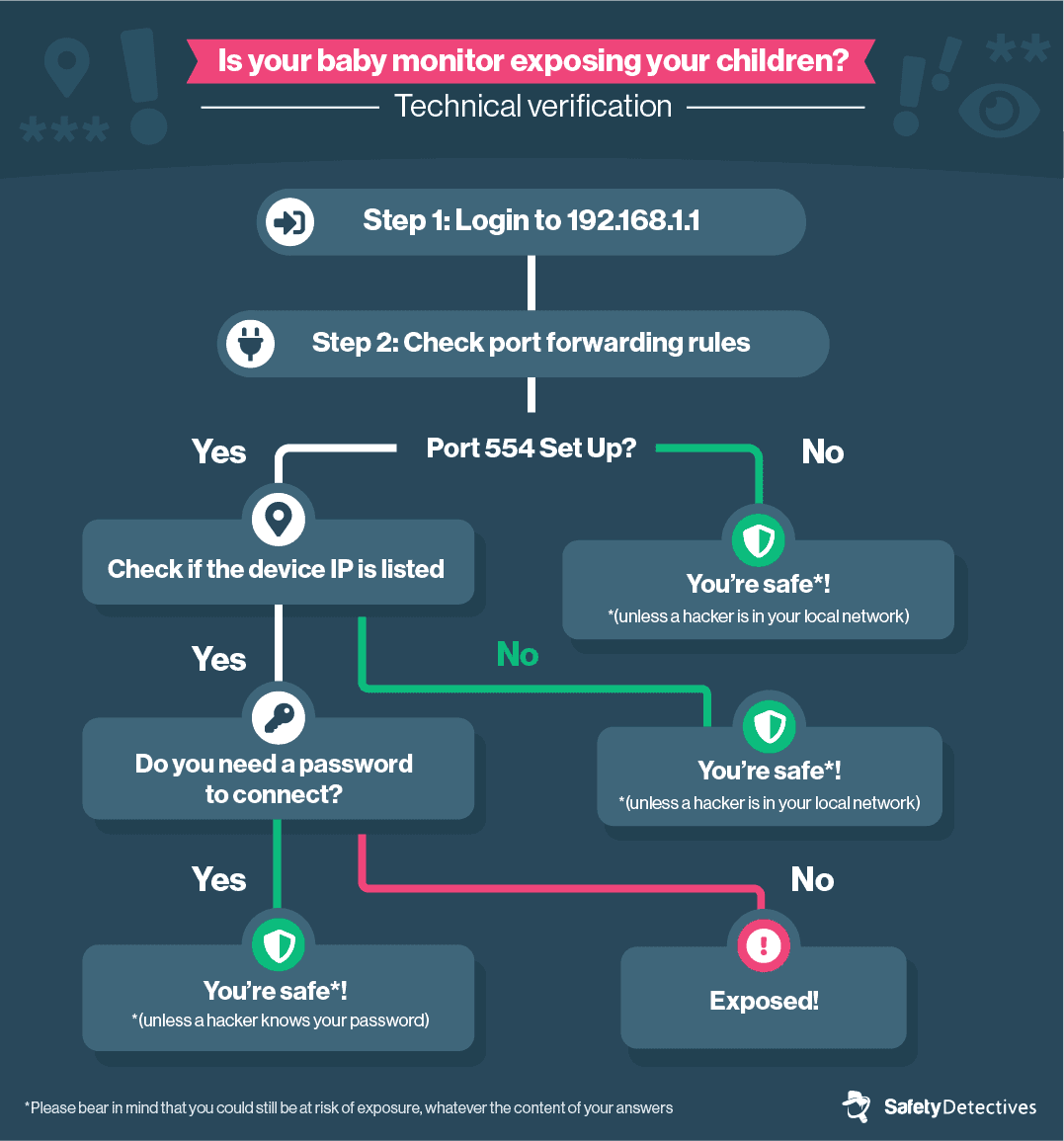
If your pathway in both guides ultimately states that you have been exposed, then there is a good chance that this is indeed the case.
Alternatively, If your answers lead you to the conclusion that ‘you’re safe,’ so too is this outcome likely to be true.
However, please bear in mind that you could still be at risk of exposure, whatever the content of your answers.
What causes this type of data exposure?
So why do some baby monitors become exposed in this manner? And what misapplications cause vulnerabilities in some RTSP cameras?
Our cybersecurity team has diagnosed 4 primary reasons why baby monitors can become unsecured, and therefore unsafe to use:
- Devices designed for local networks are streamed over the internet.
A local network is a group of devices (or computers) that are linked together in one physical location, such as a residence, an office, or a school. Local networks are therefore private, localized connections.
Many baby monitors are designed for use on local networks. This means they allow any local device to connect to their stream freely, with the assurance that the local network itself will provide enough security.
Unfortunately, if an organization (such as a daycare center) was to stream with this type of device online and the connection isn’t password-protected, there are no security procedures in place to stop anyone from gaining access to these cameras.
- Some devices can be misconfigured for use outside of a local network, without adequate authorization.
Some cameras may be designed for use within a local network, whilst also allowing a direct connection to your laptop or computer.
With this type of camera, many users fail to implement the correct security procedures (such as password protection), resulting in a baby monitor that allows unauthorized access.
- IP webcams that are repackaged as baby-monitors.
In the name of cutting-corners, various companies have been known to rebrand IP webcams as baby monitors.
This is a common occurrence within the e-commerce space, where a number of e-commerce stores wrongly advertise cameras as products that are suitable for use as a baby monitor. In most cases, the original manufacturer has not intended, nor marketed, their product for use as such.
The issue is that these webcams are designed to be used within a local network, and not online.
Should any parent tamper with the configurations of these cameras to view their video stream from outside of the home, these devices can quite easily become misconfigured, allowing unauthorized access without the owners realizing it.
- Manufacturers oversight.
Some manufacturers can unwittingly misconfigure baby monitors to become unsecured. This is often because they desire to provide a ‘pain-free’ installation process and simpler user experience for their customers.
Manufacturers also have a responsibility to warn their customers that they must secure their devices properly before taking them online. Many brands fail to warn customers in a way that is glaringly obvious, if at all.
Unfortunately, the end result of manufacturer oversight can be a slapdash product without any of the important authentication procedures.
Data Breach Impact
There are potentially hundreds of thousands of people affected by this vulnerability.
At the moment of writing, our team has discovered over 110,000 open camera streams. Of these cameras, over half of them are being used as CCTV, providing surveillance for shops, or the exterior of properties.
Around 10% of these cameras are used for viewing house interiors, like living rooms or hallways. Most of the remaining cameras are baby monitors, being used to check up on children, or as cameras in child daycare centers, or retirement homes.
Considering that there is, in all likelihood, a large number of people affected on streams within kindergarten or retirement homes, there are potentially over a hundred thousand people affected by this vulnerability. There’s also the possibility that there are hundreds of thousands of additional streams yet undiscovered, that we simply do not have the time to sift through.
Nonetheless, the impact of this vulnerability is considerable. Many of these cameras are streaming directly and indirectly identifiable information. This can include anything from images of your children to the interior of your house or daycare center. Some hackers are even able to find out the name and address of the user (through the use of additional programs).
Predators could be collecting this information and these images of your children. Criminals are also able to use these cameras to organize their criminal activities, and may even access the controls of cameras that allow rotation.
We’ve seen that pedophiles are actively searching for innocent videos of children, uploaded by their parents, so it is important to stay vigilant and follow the correct steps for securing your baby monitors.
Preventing Data Exposure
There are several steps you can take to make sure your baby monitors are safe, and will only allow access to people who are permitted to view the video stream.
First of all, you should try to set up password protection in your camera’s configuration. Many brands have a different way of doing this, and you can refer to your camera’s user guide to find out how to password protect your device. If your device does not allow you to set a password, and filter who can connect to the device, you should avoid exposing it to the internet altogether.
If you are struggling to change your camera’s password, there is another way you can safeguard it against snoopers.
First of all, you must log onto your router. This is the ‘box’ fitted in your house, that helps you connect to the internet. To log onto your router, type your router’s ‘IP address’ into your web browser. You can refer to your internet service provider for this information.
Once your router’s ‘log on’ prompt has appeared, enter your service provider’s generic username and password (if you have not changed these details). Again, this information can be found with your internet provider.
Once logged onto your router, you are looking for a setting called ‘access control’ or ‘access list.’ You need to turn this on. Whilst many providers have a different menu layout, you can find out how to locate this information in your router’s user guide.
From here you can whitelist specific IP addresses, allowing only those devices to connect. Devices attempting to connect with your router will appear in a ‘blocked’ menu, and you can simply click ‘allow’ if you wish to grant them access. You can also add whitelisted devices manually, by entering the device’s MAC address into the appropriate input field. A device’s MAC address can be found in its settings.
Do this for every device you would like to authorize, and your baby monitors are safe to use.
Of course, many of these problems can be avoided from the start. When choosing which baby monitor you would like to purchase, make sure you research each device thoroughly before buying. Don’t just rely on the brand’s images/explanation of the product; you want to make sure you are buying a legitimate baby monitor and not a repackaged wifi webcam. This is especially important when buying from reseller stores.
Although the idea of parents connecting to a kindergarten’s stream sounds useful, daycare centers should make sure their devices are secured through password protection. This password can then be shared with parents. If you are connecting freely to your daycare center’s stream, that stream could well be unsecured.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light including 400 gigabytes of scraped Facebook, Instagram and LinkedIn user data affecting over 200 million users from all over the world, as well as, around 2 million users’ information being leaked by Indian e-learning platform Edureka.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.
Published on: Feb 16, 2021