
One of the world’s well-known cosmetic brands has been informed that a significant data breach was discovered on its web server, which was found to be publicly exposed, without password protection or encryption.
Our security team, led by Anurag Sen, discovered Avon.com’s US server without encountering any security measures or protection. The vulnerability effectively means that anyone possessing the server’s IP-address could access the company’s open database.
In a statement to the market on 9 June 2020, Avon put out a statement confirming that an incident had “interrupted some systems and partially affected operations”; indicating that the statement was referencing a different issue that may, or may not, be related to the breach discovered by our security team.
A few days later, Avon submitted a second regulatory filing declaring that no financial data was involved “as its main e-commerce website does not store that information”. The company has also confirmed that its various online operations around the world remain in various stages of recovery, with some regions operating normally, while others are still offline.
Who is Avon.com?
First established in 1886, the website’s parent company, New Avon Company, is a leading social selling beauty company operating in North America, Puerto Rico and Canada. However, the company is headquartered in London, UK.
Avon’s product portfolio includes award-winning skincare, color cosmetics, fragrance, and personal care products, featuring iconic brands such as ANEW, Avon Color and Skin So Soft, as well as fashion products and accessories.
In May 2019, Brazilian company Natura & Co announced its intent to acquire a 76% stake in Avon with the deal being completed in January 2020. Coincidentally, Natura & Co was embroiled in its very own cybersecurity debacle in April this year.
The transaction created the world’s fourth-largest “pure-play” beauty company that intends to court millions of customers worldwide.
According to Natura & Co, by combining the Avon, Natura, Body Shop and Aesop brands under one roof, the group company is set to become an “unparalleled leader” in the direct-to-consumer space, serving over 200 million consumers globally every year.
What was leaked?
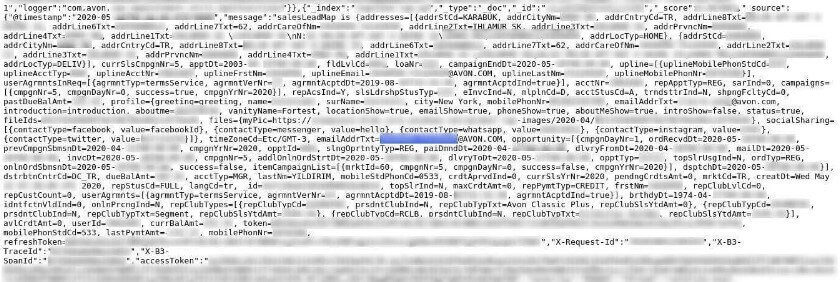
Avon.com’s server contained API logs for the company’s web and mobile sites which meant the data breach exposed all production server information including internal “OAuth tokens”.
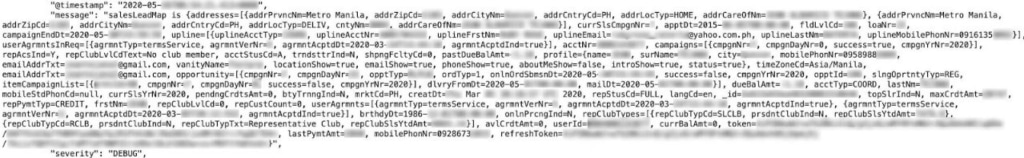
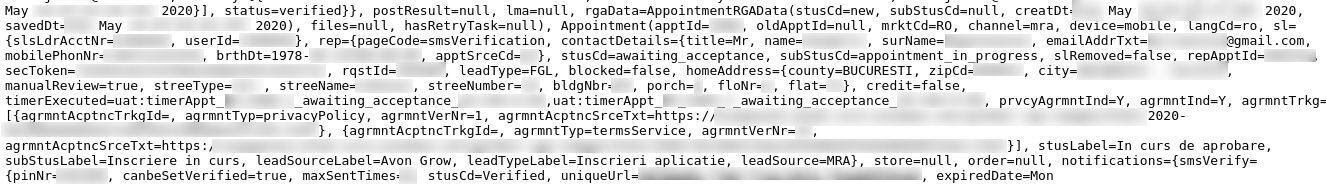
Data breach shows various details regarding over 40,000 security tokens
Similar to access tokens, OAuth tokens are used for sign-in purposes, with the key difference being that they expire after a limited time. Therefore, users must generate refresh tokens to obtain a new OAuth token. In the case of Avon.com’s server vulnerability, both the sign-in and refresh tokens were exposed, which is sufficient for malicious hackers to obtain full access to an account.
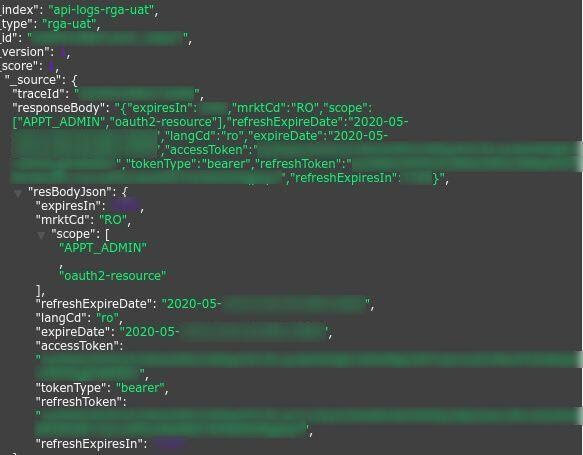
Log showing Oauth tokens and access tokens
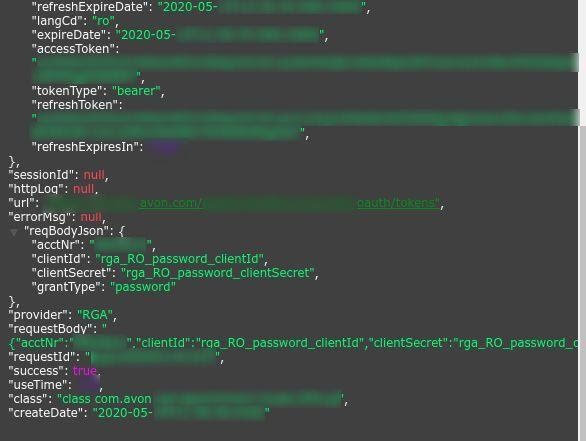
Log showing Oauth tokens and access tokens
Moreover, Avon’s server also contained internal logs that could be repurposed by nefarious users to harm Avon’s IT infrastructure. Hackers could potentially harness the server to mine cryptocurrency, plant malware, or conduct ransomware attacks upon the server owners.
However, it is important to note that, at this stage, it remains unclear whether Avon’s server vulnerability and its extensive operational issues in recent weeks are connected.
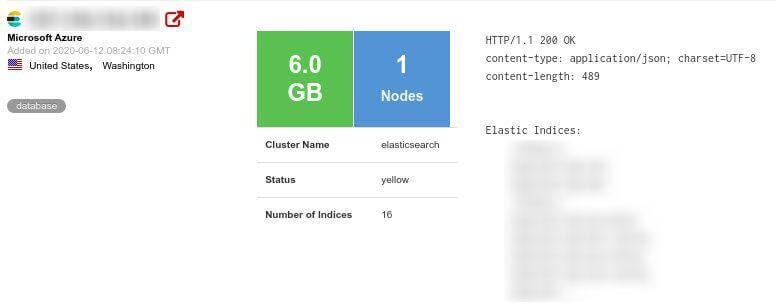
Initially, our security team discovered close to 6 GB of data, although this figure has since risen as more information became available. At last count, Avon.com’s database contained over 7 GB of data and more than 19 million document records.
According to our security team, Avon.com’s cybersecurity vulnerability first surfaced on 3 June 2020 and was subsequently discovered by our operatives on 12 June 2020. Following the discovery, our team made direct contact with Avon representatives, with the company able to secure the server shortly thereafter.
Our security team was able to discover the following personally identifiable information from Avon.com’s server:
- Full names
- Phone numbers
- Dates of birth
- Email addresses
- Physical addresses
- GPS coordinates
- Last payment amounts
- Names of company employees (suspected but not confirmed)
- Administrator user emails
The server also contained non-personal technical information such as:
- 40,000+ security tokens
- OAuth tokens
- Internal logs
- Account settings
- Technical server information
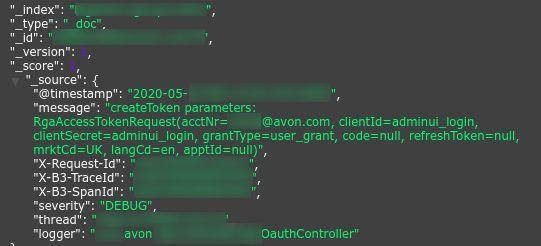
Internal log showing internal employee details
The server also contains SMS verification service logs:
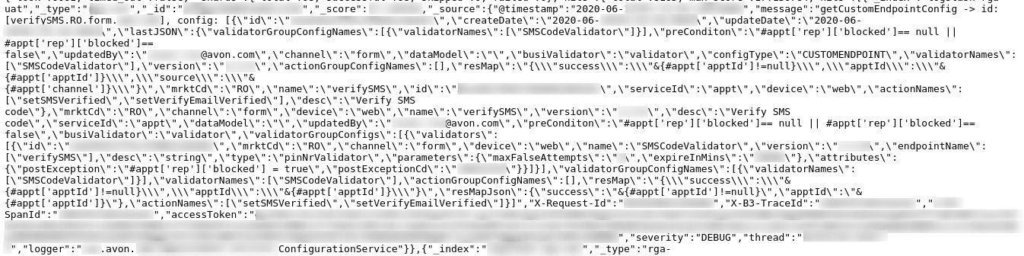
From index logs, our security team was able to find the following tallies:
- More than 665,000 technical log entries, including token values and internal resources such as APIs,
- Almost 3 million technical log entries and errors including private/sensitive information such as login PIN codes sent by SMS, dates of birth, and phone numbers,
- 11,000+ entries marked as “salesLeadMap”, showing values such as full names, addresses, account settings, dates of birth, token values, last payment amounts, and GPS coordinates,
- Approximately 780,000 technical log entries exposing potentially sensitive technical information, such as administrator user emails and what seems to be a list of admin system permission categories,
- Close to 450,000 technical log entries and application/Java errors, potentially exposing sensitive technical information about the server.
Data Breach Impact
Avon.com’s server breach poses several potential dangers to affected users.
First and foremost, exposed details could potentially be used to conduct identity fraud across different platforms and institutions. Users’ contact details could be harnessed to conduct a wide variety of scams while personal information from the leak could be used to encourage click-throughs and malware downloads. Personal information is also used by hackers to build up rapport and trust, with a long-term view of carrying out a larger magnitude intrusion in the future.
Worryingly, the leak exposed reams of technical logs which could be used to not only target Avon customers but also Avon’s IT infrastructure directly, thereby leading to further security risks and financial ramifications.
Given the type and amount of sensitive information made available, hackers would be able to establish full server control and conduct severely damaging actions that permanently damage the Avon brand; namely, ransomware attacks and paralyzing the company’s payments infrastructure.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you are not a victim of attacks – cyber or real-world – if your data gets leaked?
- Be cautious of what information you give out and to whom.
- Check that the website you are on is secure (look for https and/or a closed lock).
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.).
- Create secure passwords by combining letters, numbers, and symbols.
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be.
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust.
- Avoid using credit card information and typing out passwords over unsecured Wi-Fi networks.
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware.
About Us
is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro-bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data.
Published on: Jul 28, 2020