
Updated on: September 23, 2024
Short on time? Here’s how to remove the browser hijacker:
- Remove Suspicious Apps and Extensions. Uninstall any recently installed apps or browser extensions that you don’t trust.
- Scan Your PC. Run a “Full System Scan” with a top-notch antivirus (Norton is the best).
- Remove Virus. Once the scan is complete, let the antivirus remove any malicious or potentially unwanted programs it finds.
- Stay Safe. Protect yourself from further threats by using a high-quality antivirus with good internet security features (Norton is my top choice).
If you’re getting strange redirects or seeing ads popping up everywhere, then there’s a good chance that you might be dealing with a browser hijacker. This annoying malware changes your browser settings without asking you. It sneaks in with free downloads or dubious links to steal your information and show you endless ads.
The good news is, getting rid of a browser hijacker isn’t too hard. This guide will show you how to do it in 3 simple steps, helping you clean up your browser and keep your online sessions safe. We’ll go through how to spot these hijackers, kick them out, and make sure they don’t come back.
For the best protection, I recommend Norton. It’s an excellent choice for removing all malware types including browser hijackers. Plus, it comes with a 60-day money-back guarantee, so you can try it risk-free.
Preliminary Step: Uninstall Recent Apps & Extensions
Before we begin, you need to remove any recently installed apps and extensions causing the browser hijacker. If you’re not sure how to do this, simply click on the relevant link for the operating system or browser you are using:
- Uninstall Recently Installed Applications on Windows 11.
- Uninstall Recently Installed Applications on Windows 10.
- Uninstall Recently Installed Applications on Mac.
- Uninstall Recently Installed Applications on Linux.
- Uninstall Recently Installed Applications on Android.
- Uninstall Recently Installed Applications on iOS.
Uninstall Recently Installed Applications on Windows 11
- Left-click on the Start button on the taskbar.
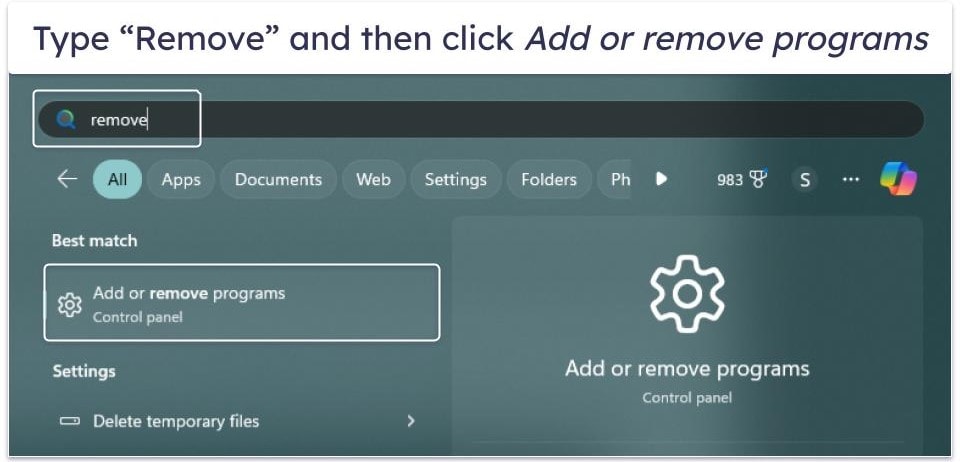
- Type “Remove” into the search for apps, settings, and documents field.
- Click Add or remove programs under the Best match category.
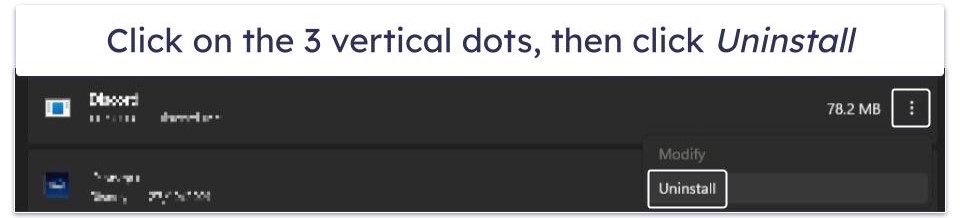
- In the window that appears, find the suspicious application you want to uninstall and click the 3 dots to its right. Select Uninstall from the drop-down menu.
- Follow the uninstall wizard’s instructions.
- Next, remove any suspicious extensions from your browser:
- Remove suspicious extensions on Chrome.
- Remove suspicious extensions on Firefox.
- Remove suspicious extensions on Edge.
- Remove suspicious extensions on Safari.
Uninstall Recently Installed Applications on Windows 10
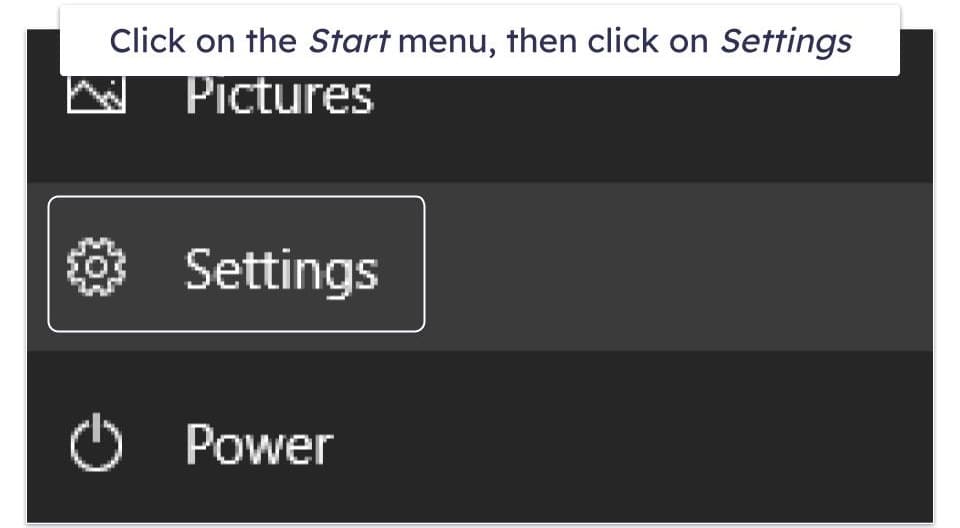
- Click on Settings in your computer’s start menu. This will bring up the Windows 10 settings menu.
- In the next window that opens, click on Apps.
- Scroll through the list, and click Uninstall on any apps you don’t trust.
- Follow the uninstall wizard’s instructions.
- Now, you need to remove suspicious extensions from your browser:
- Remove suspicious extensions on Chrome.
- Remove suspicious extensions on Firefox.
- Remove suspicious extensions on Edge.
- Remove suspicious extensions on Safari.
Uninstall Recently Installed Applications on Mac
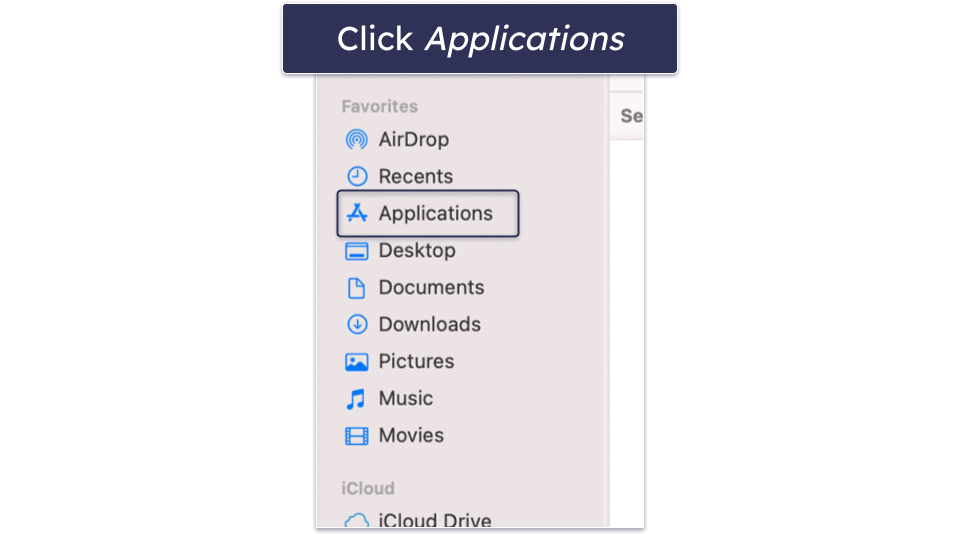
- Open Finder from your Mac’s dock.
- Select Applications.
- Scroll down the list and drag any app you don’t trust over the trash icon on your Mac’s dock.
- Next, click and hold the trash icon until Empty Trash appears. Then, click Empty Trash.
- You’re now ready to remove suspicious extensions from your browser:
- Remove suspicious extensions on Chrome.
- Remove suspicious extensions on Firefox.
- Remove suspicious extensions on Edge.
- Remove suspicious extensions on Safari.
Uninstall Recently Installed Applications on Linux
- Launch Ubuntu Software Center and navigate to the Installed tab.
- Scroll through the list of apps, looking for any app that seems suspicious.
- Click the Remove button for any apps you want to get rid of. Enter your account password to confirm the action. Next, install a top antivirus for Linux to keep your computer protected in the future.
Uninstall Recently Installed Applications on Android
- Go to your device’s Settings menu.
- Go to the Apps section.
- Scroll down until you find the suspicious app and tap on it.
- Tap Uninstall and confirm your choice.
- Continue to scan your device with an antivirus.
Uninstall Recently Installed Applications on iOS
- Find the app you think might be malicious.
- Tap and hold its icon.
- A red option saying “Remove App” will appear.
- Tap it, confirm the action, and the app will be uninstalled from your device.
- Keep your device from getting reinfected.
Remove Suspicious Extensions From Chrome
- Click on the 3 vertical dots in the top right corner of the browser screen.

- Click Extensions > Manage Extensions.

- Scroll through the list of installed extensions until you see the suspicious one(s) you want to uninstall, then click Remove.

- If this resolves your issue, you can scan your computer with an antivirus program. However, if you’re still having problems, you need to reset your web browser. Click on the relevant link below to learn how:
Remove Suspicious Extensions From Edge
- Click on Extensions, followed by Manage extensions.

- Scroll through the list of installed extensions until you see the suspicious one you want to uninstall, then click Remove.

If the issue persists, you need to take further steps. However, if the issue is resolved you can simply scan your computer with an antivirus program.
Your alternative is to reset your browser to its default settings to completely restore it — but be aware this will delete all of your extensions. Click on the browser you use to learn how:
Remove Suspicious Extensions From Firefox
- Click on the icon on the top right that looks like a puzzle piece to open the Add-ons Manager.

- Click on Extensions.

- Find any suspicious extensions, click the 3 horizontal dots to their right, and then select Remove.

- Once this is done, the issue should be resolved and you can move onto scanning your computer. If you’re still having problems, you need to reset your browser. To do this, click on the browser you use:
Remove Suspicious Extensions From Safari
- Open Safari, then click the Safari button in the upper-right corner of the screen and select Settings (or Preferences).

- In the newly opened window, find and click the Extensions tab.
- Scroll through the list of installed extensions until you see the one you want to uninstall, then click Uninstall.

- You’re now ready to scan your system.
Resetting Your Browser to Default Settings
For Chrome Users:
- In the upper-right corner, click the 3 vertical dots, then click Settings.
- From the bar on the left, click Reset settings.

- Next, choose Restore settings to their original defaults and confirm your choice in the box that pops up. You’re now ready to scan your computer.

For Edge Users:
- Launch Edge and click the 3 horizontal dots at the top right of your browser, then Settings.

- Click Reset Settings in the bar on the left.

- Click on Restore settings to their default values. Once you’ve restored your browser to its default settings, you can scan your computer with a trusted antivirus.

For Firefox Users:
Instead of having to completely reset your browser, Firefox allows you to refresh your browser and keep information like your passwords and bookmarks:
- Click on the 3 horizontal bars on the top right of your screen and click Help.
- Click on the More troubleshooting information option.

- Click Refresh Firefox…, then confirm your choice by clicking Refresh Firefox.

For Safari Users:
- Click on the Safari menu and select Preferences.
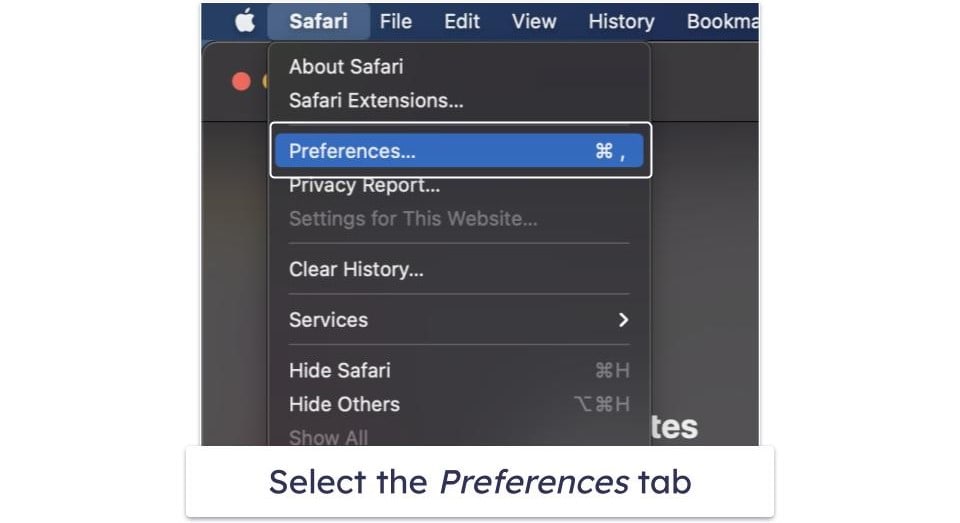
- Click on the Privacy tab, then select Manage Website Data…

- Choose Remove All to completely clear your browser data, then confirm your choice by clicking Remove Now. Now you can scan your system.

Step 1. Identify the Browser Hijacker With Your Antivirus (And Don’t Make the Problem Worse!)
Unplug your tablet, cell phone, or any removable storage devices from your computer. If your computer is infected with malware, it can spread to the removable storage devices and reinstall itself later on.
Run a full disk scan after downloading an antivirus, even if you’ve already removed suspicious add-ons from Chrome or think you have located the malware files on your computer. Malware can replicate and hide throughout your PC in multiple copies. Running a full disk scan will help you find, quarantine, and delete every copy of malware causing the browser hijacker issue. It will also remove any other malware, including spyware, rootkits, and trojans, from your computer.

Don’t stop the scan until it is complete, even if you see viruses you recognize in the list of infected files. The full disk scan can take up to 3–4 hours as the antivirus needs to check every file and process on your PC. It’s best to leave it to finish.
If you perform CPU-intensive activities during the scan, your computer may slow down. To avoid this, it’s best to run the scan overnight or when you’re not using your computer. Some antiviruses, such as Norton, allow you to schedule scans, making it easier to organize. Once your antivirus has completed the malware scan, any instances of malware will be quarantined. You can now proceed to step 2.
Step 2. Remove the Browser Hijacker Infection and Delete Any Other Infected Files
If your antivirus detects potentially harmful files, it will take you to its quarantine folder. In this folder, you will find a list of all the flagged files. Carefully review this list and identify the safe files before taking any action. Your antivirus may have mistakenly identified false positives as threats. That said, only keep files you’re 100% certain are safe and remove the rest. If you are unsure about a particular file, contact your antivirus’s customer support team before making any decisions.

Once all the detected files are removed or whitelisted, restart your device. After restarting, you should run a second full disk scan to ensure that there are no traces of malware left. The second scan won’t take as long as the first one because many antiviruses remember recently scanned files and only check new or modified ones.
After the second scan, there shouldn’t be any flagged files. But if you still find files listed in the quarantine folder, you’ll have to repeat steps 1 and 2 until you can scan your computer without detecting any issues.
Finally, check if your web browser is functioning normally. If it isn’t, you may have to repeat the preliminary step to reset your web browser to its default search engine.
It’s time to begin step 3. There are many other malware files available online that could spread through your Wi-Fi network, compromise your online accounts, and harm your computer. Therefore, it is important to ensure that your device is fully protected against all such threats.
Step 3. Keep Your Device From Getting Re-Infected
Cybercriminals release new malware all the time, and if you aren’t protected, you’re always vulnerable to data theft, identity theft, and other potential risks. However there are several ways to keep your devices and data safe. Here’s what you need to do:
- Keep Your Software, OS, and Drivers Up-To-Date: You should regularly update your operating system, software, and drivers to protect your devices from online threats. Using outdated software makes your system vulnerable to cyberattacks, and it makes it easier for criminals to inject your device with malware. To minimize these risks, it’s highly recommended that you enable automatic updates whenever possible and consistently check for new versions of your software, operating system, and drivers. Some antiviruses even offer vulnerability scanners that automatically ensure your computer is running the latest software versions. By being proactive and staying up-to-date, you can increase your device’s security and keep it running smoothly.
- Avoid Downloading Suspicious Files: Malware often sneaks into your devices through dubious emails and untrustworthy websites. To ensure your safety, it’s important to avoid clicking on suspicious links and refrain from downloading attachments from unknown senders. Even in cases where you know the sender personally, it is advisable to verify their complete email address before opening any attachments. Also, make sure to have an antivirus program with real-time protection (such as Norton or Bitdefender) installed on your device. This way, files, websites, and emails will be constantly scanned for harmful content, and any unsafe downloads will be blocked.
- Secure Your Wireless Network and IoT Devices: It’s important to secure your Wi-Fi network and Internet of Things (IoT) devices to protect your personal information. You can do this by creating a strong password for your wireless network, which is easy to do with a good password manager like 1Password. Once you’ve created a password, make sure your network is secure by checking the lock icon next to its name. Also, be sure to check the manual or search online for instructions on how to set up passwords for your IoT devices. Finally, for public Wi-Fi connections, always use a high-quality VPN such as ExpressVPN to protect your data from potential threats.
- Download a Secure Antivirus Program: Having a reliable antivirus is crucial to prevent malware such as viruses, ransomware, and phishing attacks. With an antivirus, you can perform a full system scan to keep your device safe and enjoy additional features like a strong firewall, real-time scanning, and automatic updates. Norton is a great choice because it offers 100% malware detection, a wide range of extra features (such as a smart firewall), and an easy-to-use interface.
3 Best Antivirus Programs for Removing a Browser Hijacker
Quick summary of the best antiviruses for removing a browser hijacker:
- 🥇 1. Norton — Best antivirus for removing a browser hijacker completely in 2024.
- 🥈 2. Bitdefender — Cloud-based antivirus with useful extra features and tools.
- 🥉 3. TotalAV — Beginner-friendly antivirus that’s great for new users.
Signs You Have a Browser Hijacker on Your Device
Some signs can indicate the presence of a browser hijacker on your device — being aware of these signs can help you find and remove it quickly and protect your device. Here are signs to look out for:
- Suspicious search engine — A browser hijacker may replace your default search engine, such as Google or Bing, with a malicious one, such as Search Marquis.
- Redirects to unwanted websites — Malicious sites use browser hijackers to drive traffic to increase ad revenue, steal user information, or infect their devices with more harmful malware.
- Too many pop-up ads — If your device is infected with this malware, you may encounter a ton of ads. These ads may appear on redirected websites, alternative search engines, or even follow you around legitimate websites.
- A different homepage — If your browser’s homepage has changed to another one filled with ads without your consent, a browser hijacker could be responsible.
- Unrecognized extensions — If you encounter unfamiliar browser extensions along with strange ads, remove them immediately and scan your device.
Examples of Browser Hijackers
- Ask Toolbar — This browser add-on was often bundled with other free software downloads and could change your default browser’s home page to Ask.com or insert the Ask Toolbar, redirecting search results and showing ads.
- Babylon Toolbar — Known for changing search engine results and browser home pages to Babylon’s own website or search domain. The toolbar is often bundled with other software and can be difficult to remove.
- CoolWebSearch (CWS) — A series of browser hijackers that exploit vulnerabilities in Microsoft’s Internet Explorer, redirecting search engine queries to various websites full of advertisements.
- Conduit Search/Toolbar — Usually bundled with other free software downloaded from the internet. Once installed, it may change the home page and search engine of installed browsers to Conduit Search without permission.
- Snap.do — Alters your default web browser settings to display intrusive ads and scammy pop-ups, leads to dubious websites, or redirect you through an alternative search engine, like Snap.do. It’s often disguised as a web browser extension.
Tips for Avoiding Browser Hijackers
Browser hijackers ruin your online experience by changing browser settings without your permission, resulting in unwanted redirects and ads. Here’s how you can protect your PC from getting infected with browser hijackers:
- Use a reliable antivirus — Top antiviruses like Norton come with many features to protect your computer from malware, including real-time protection to prevent viruses from causing damage, a smart firewall to protect your network, and web protection tools to help you stay safe from dangerous websites.
- Be cautious when clicking on links — Avoid clicking suspicious links from unknown or untrusted sources in pop-up ads, emails, or social media posts. Always check the source of links before clicking.
- Download software from trusted sources — Always make sure that your downloads come from reputable sources, such as official app stores or directly from software publishers, to avoid accidentally downloading malware.
- Keep your computer and drivers updated — You should keep your operating system, web browser, and other software up to date with the latest security patches and updates. Doing so helps to patch any known vulnerabilities that could be exploited by redirect viruses.
- Use a VPN — A Virtual Private Network (VPN) secures your internet connection by encrypting the data you send and receive. This not only keeps your online activities private but also makes it more difficult for hijackers to target your browser with malicious redirects.
- Read before installing software — Pay attention to the permissions and details when installing new software to avoid unintentionally adding a hijacker to your system.
- Be careful with browser extensions — Only add extensions from sources you trust and regularly check your browser settings for unexpected changes.
- Use an ad blocker — A reliable ad blocker can protect you from pop-up ads and prevent redirects to dangerous websites, making your online experience safer.
Frequently Asked Questions
What is a browser hijacker and how does it work?
A browser hijacker is a type of malware that modifies a web browser’s settings without your permission, typically changing the default homepage, search engine, and sometimes the new tab page. It works by redirecting you to specific websites to increase advertising revenue or spread malware. Browser hijackers often come bundled with free software downloads, email attachments or compromised websites. They can also install unwanted toolbars or extensions, and track user activity for targeted advertising.
Are browser hijackers easy to remove?
Yes, browser hijackers are generally easy to remove with the help of reputable antivirus like Norton.
Norton can effectively detect and neutralize browser hijackers by scanning incoming internet traffic for malicious elements and performing full system scans to identify and remove any existing hijackers. However, while antivirus software like Norton can remove browser hijackers, some manual steps may still be required for complete removal.
What is the most unsafe browser?
It really depends on what you’re looking for in a web browser. For example, while it’s safe, Google Chrome has faced criticism for collecting user data, and its popularity makes it a frequent target for cybercriminals.
In contrast browsers like Brave and Tor are privacy focused browsers. Brave automatically blocks ads and trackers by default. It also has HTTPS Everywhere, script blocking, and fingerprinting protection. Tor Browser is designed for anonymous browsing and is built on the Tor network, which routes your internet traffic through multiple layers of encryption. While it may be slower than other browsers, it’s one of the best options for privacy and anonymity.
Can I remove a browser hijacker manually or do I need antivirus software?
Removing a browser hijacker manually can be challenging without technical expertise, as these malware types can hide in system files, registry entries, and browser settings. Antivirus software is recommended for effectively detecting and eliminating browser hijackers and their associated components. Top antivirus solutions like Norton 360, stay updated with the latest virus definitions and have advanced scanning capabilities to ensure a thorough cleanup. They also offer ongoing protection against future threats, making them a more reliable choice for dealing with browser hijackers.